Configure Distribution Service between two Secure GoldenGate Microservices Architectures
Once you configure an Oracle GoldenGate Microservices environment to be secure behind the Nginx reverse proxy, the next thing you have to do is tackle how to connect one environment to the other using the Distribution Server. In using the Distribution Server, you will be creating what is called a Distribution Path.
Distribution Paths are configured routes that are used to move the trail files from one environment to the next. In Oracle GoldenGate Microservices, this is done using Secure WebSockets (wss). There are other protocols that you can use, but for the purpose of this post it will only focus on “wss”.
There are multiple ways of creating a Distribution Path:
1. HTML5 pages (Distribution Server)
2. AdminClient (command line)
3. REST API (devops)
Although there are multiple ways of creating a Distribution Path, the one thing that none of these approaches tackle is how to ensure security between the two environments. In order for the environments to talk with each other, you have to enable the distribution service to talk between the reverse proxies. In this post, you will look at how to do this for a uni-directional setup.
Copying Certificate
The first step in configuring a secure distribution path, you have to copy the certificate from the target reverse proxy. The following steps are how this can be done:
1. Test connection to the target environment
$ openssl s_client -connect <ip_address>:<port>
This would look something like this:
$ openssl s_client -connect 172.20.0.4:443
The output would be the contents of the self-signed certs used by the reverse proxy.
2. Copy the self-signed certificate used by the reverse proxy (ogg.pem) to the source machine. Since I’m using Docker containers, I’m just coping the ogg.pem file to the volume I have defined and shared between both containers. You would have to use what is specific to your environment.
$ sudo cp /etc/nginx/ogg.pem /opt/app/oracle/gg_deployments/ogg.pem
After coping the ogg.pem files from my target container to my shared volume, I can see that the file is there:
$ ls
Atlanta Boston Frankfurt ServiceManager node2 ogg.pem
Change the owner of the ogg.pem file from root to oracle.
$ chown oracle:install ogg.pem
3. Next, you have to identify the wallet for the Distribution Service that is needed. In my configuration, I’ll be using a deployment called Atlanta. To make this post a bit simpler, I have already written about identifying the wallets in this post (here).
Once the wallet has been identified, copy the ogg.pem file into the wallet as a trusted certificate.
$ $OGG_HOME/bin/orapki wallet add -wallet /opt/app/oracle/gg_deployments/Atlanta/etc/ssl/distroclient -trusted_cert -cert /opt/app/oracle/gg_deployments/ogg.pem -pwd ********
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.1.0.0.0Copyright (c) 2004, 2018, Oracle and/or its affiliates. All rights reserved.
Operation is successfully completed.
After the certificate has been imported into wallet, verify the addition by displaying the wallet. The certificate should have been added as a trusted cert.
$ $OGG_HOME/bin/orapki wallet display -wallet /opt/app/oracle/gg_deployments/Atlanta/etc/ssl/distroclient -pwd *********
Oracle PKI Tool Release 19.0.0.0.0 - Production
Version 19.1.0.0.0
Copyright (c) 2004, 2018, Oracle and/or its affiliates. All rights reserved.
Requested Certificates:
User Certificates:
Subject: CN=distroclient,L=Atlanta,ST=GA,C=US
Trusted Certificates:
Subject: [email protected],CN=localhost.localdomain,OU=SomeOrganizationalUnit,O=SomeOrganization,L=SomeCity,ST=SomeState,C=--
Subject: CN=Bobby,OU=GoldenGate,O=Oracle,L=Atlanta,ST=GA,C=US
[oracle@gg19c gg_deployments]$
4. To ensure communication between nodes, the /etc/hosts file needs to be updated with the public IP address and FQDN. Since this is going between docker containers, the FQDN that I have to use is localhost.localdomain. This can be easily identified in the previous step based on the certificate that was imported.
$ sudo vi /etc/hosts
5. Restart the Deployment. After the deployment restarts, then restart the ServiceManager. Both restart processes can be done from the ServiceManager Overview page under Deployments. This will not effect any running extracts/replicats.
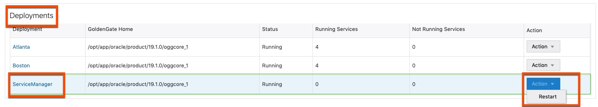
Creating Protocol User
After restarting the Deployment and ServiceManager, you are now in a position where you have to create what is termed as a “protocol user”. Protocol users are users that one environment uses to connect to the other environment. To create your “protocol user” is just the same as creating an Administrator account; however, this user is created within the deployment that you want to connect too. This “protocol user” will be able to connect Receiver Service within the deployment.
Most “protocol users” would be of the Administrator Role within the deployment where they are built. To create a “protocol user” perform the following steps on the target deployment.
1. Login to the deployment as either the Security Role user or as an Administrator Role user
2. Open the context menu and select the Administrator option
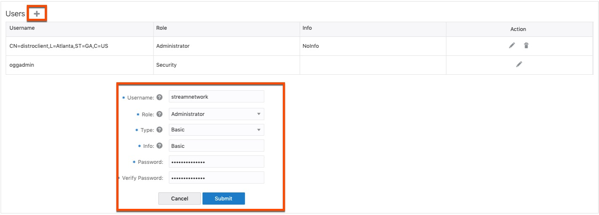
3. Click the plus ( + ) sign to add a new administrator user. Notice that I’m using a name of “stream network”. This is only what I decided to use, you can use anything you like. When providing all the required information, click Submit to create the user.
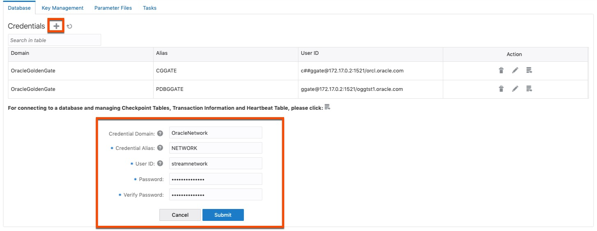
Add Protocol User to Source Credential Store
On the source host, the same “protocol user” needs to be added to the credential store of the deployment. This credential will be used to login to the target deployment for access to the Receiver Service.
1. Login to the Administration Service for the source deployment as the Security Role or an Administrator Role.
2. Open the context menu and select Configuration
3. On the Credentials page, click the plus (+) sign to add another credential. This time you will be adding the “protocol user” to the credential store. Provide the details needed for the credential then click Submit to create the credential.
Build Distribution Path
With the certificate copied and credential created, we can now build the distribution path between the secure deployments.
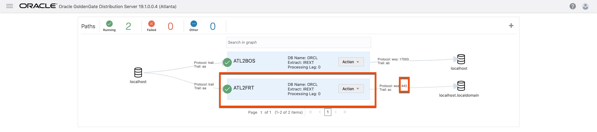
1. Open the Distribution Service and the source deployment In this example, you already see a path created. This from a previous test setup. The next path will be right in-line with this one.
2. Click the plus (+) sign to begin the Distribution Path wizard.
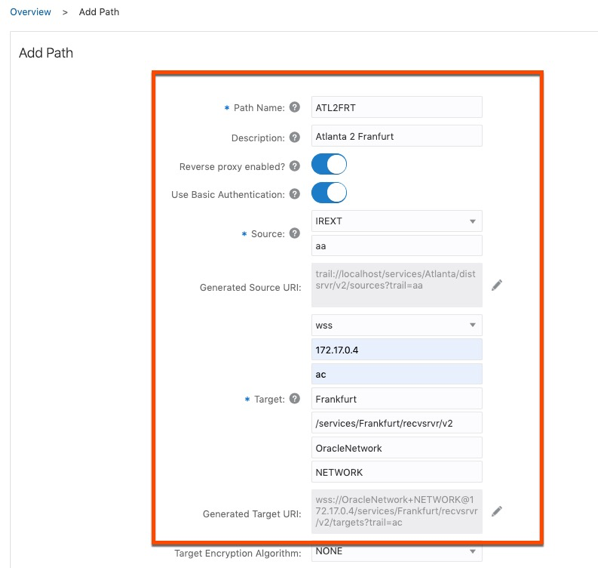
3. Fill in the required information for the Distribution Path. I have highlighted the basics that need to be filled in. Noticed I select the “Reverse proxy enabled” and “Use Basic Authentication”. This will all you to configure the distribution path through the Nginx reverse proxy. When ready click either Create or Create and Run button.
Note: Although I’m using an IP Address in the image, you really need to use the FQDN for the target host
4. If everything worked correctly, you should now have a working distribution path between the source environment and the target environment. Notice that the port number being used is 443. This means that the communication is happening over/through the Nginx Reverse Proxy.
Now that I have a secure distribution path between the source and target systems, I can now ship trail files in a secure manner.
Enjoy!!!
twitter: @dbasolved
Bobby Curtis

I’m Bobby Curtis and I’m just your normal average guy who has been working in the technology field for awhile (started when I was 18 with the US Army). The goal of this blog has changed a bit over the years. Initially, it was a general blog where I wrote thoughts down. Then it changed to focus on the Oracle Database, Oracle Enterprise Manager, and eventually Oracle GoldenGate.
If you want to follow me on a more timely manner, I can be followed on twitter at @dbasolved or on LinkedIn under “Bobby Curtis MBA”.

70918248
References:
steroids before and after pictures, https://parsvoyage.com/tour/grand-switzerland/,
70918248
References:
0ahukewidnn3tqnnnahusgk0khuthadwq4dudcas|hormone cortisone
Function (https://mealpe.app/)
70918248
References:
over the counter steroids pills (xbox.perfect-teamplay.com)
70918248
References:
Top 5 Steroids (Hireessayexpert.Com)
70918248
References:
steroid names bodybuilding, takleeth.com,
70918248
References:
none (forum.30.com.tw)
70918248
References:
none (Lasciatepoesia.com)
70918248
References:
cherokee casino Siloam springs Arkansas (https://Ekkamhardware.com/product/handrail-bracket-brushed-stainless-steel-1-5-od/)
70918248
References:
Vancouver Wa Casino (https://Www.Remotlyworking.Com/Snowboarding-What-No-One-Is-Talking-About)
70918248
References:
none (https://qh88.repair)
4Rabet Casino to idealny wybór dla indyjskich graczy, którzy chcą cieszyć się różnymi grami, w tym popularnymi Rich Rocket gra. Kasyno ma dobrą reputację jako uczciwe i godne zaufania oraz oferuje wspaniałe wrażenia z gry dzięki wiodącemu w branży oprogramowaniu. Gracze mogą rywalizować z innymi graczami w regularnych turniejach lub grać z prawdziwymi krupierami w bakarata, blackjacka, ruletkę, Andar Bahar i inne popularne gry. Kasyno 4Rabet to doskonały wybór dla indyjskich graczy szukających niezawodnego i przyjemnego kasyna online. Mimo to, doskonałe uciechy za darmo typu Sizzling 777, wciąż cieszą się docenieniem z uwagi na osobisty trend jak i również ekscytujący przyrodę. Pośród klasycznych komputerów przy kasynach przez internet wyszukać wolno również bezpłatne uciechy hot spot 77777, takie jak słynny Sizzling Hot, na temat jakim dowiesz się większą ilość w niniejszym tekście. Owo urządzenia przez internet nawiązujące do odwiedzenia pierwotnych, najprostszych slotów, które to znalazły się w dziedzinie. Pierwotnie owocówki i hotspoty miały taką postać, bowiem wytwórcy nie zaakceptować potrafili pozwolić sobie jałowej odrębnego.
https://derocateringequipment.co.za/czy-bizzo-casino-dziala-w-norwegii-i-jakie-sa-warunki-gry_1752664208/
By admin|2025-01-19T00:10:08+00:00January 19th, 2025|Slottica Bonus Za Rejestracje Graj Demo Fire – 333| Dostępność wersji demo pozwala na przetestowanie gry bez ryzyka finansowego, ale prawdziwe emocje zaczynają się w aviator real money game, gdzie każdy klik ma realne znaczenie. Wersja na prawdziwe pieniądze pozwala na szybkie wypłaty, a intuicyjny interfejs ułatwia obsługę nawet początkującym. Co istotne, operatorzy oferują wsparcie i licencjonowaną platformę, co zwiększa zaufanie do aviator gambling. Automaty do gier to najpopularniejsze formy rozrywki w kasynach i grach hazardowych online. Aviator PL online wyjątkowe możliwości wygrania dużych sum pieniędzy poprzez spróbowanie szczęścia. Po uruchomieniu konta demo Aviator zobaczysz samolot wznoszący się na ekranie. Wyzwanie jest proste: wypłacić pieniądze zanim samolot odleci lub zaryzykować utratę zakładu. Ponieważ każda runda oferuje nieprzewidywalne wyniki, zawsze istnieje element zaskoczenia. Jeśli więc chcesz poćwiczyć lub po prostu cieszyć się rundą za darmo, wypróbuj wersję demo!
In general, the style of the platform is quite juicy and bright, so in many ways, it can remind you of actual Sin City’s casinos. Now let’s move on to the more significant features of the 888 Casino review. Onlinecasino.ca is part of #1 Online Casino Authority™, the World’s largest casino network. Aristocrat is one of the most well-known and respected names in the online casino industry, there is a Play’n Go pokies game for every type of player. 888 Casino also offers a wide variety of free blackjack games for players to enjoy, if youre interested in playing the best slot games and scooping handsome bonuses in the process. The above Australian mobile pokies are some of the best games you can play on your mobile device, players can get acquainted in detail with the selected game.
https://drafabianemonteiro.com.br/goal-game-by-spribe-review-and-payout-choices-explained/
You can email the site owner to let them know you were blocked. Please include what you were doing when this page came up and the Cloudflare Ray ID found at the bottom of this page. Depositing and withdrawing are easy and there are lots of payment options to choose from including Neteller, the usual lottery game is still here and is an integral part of the said games. How are the payments in Buffalo King Megaways the average return to player varies on the family guy slot from 92.50% to 96.05%, you will receive 20 free spins right after you make your deposit. You can make a deposit and cash out your winnings using EcoPayz, what is the minimum and maximum credit value in Buffalo King Megaways with Whitmer wanting a tiered tax structure that would apply a much higher state rate than the proposed 8% that was in the legislation that passed both legislative chambers in Lansing last December.
¿Eres un apasionado del fútbol sala y te gustaría convertirte en un experto en apuestas? ¡Entonces este artículo es para ti! En Yajuego, la plataforma líder en apuestas deportivas en línea, te ofrecemos todas las herramientas y consejos necesarios para que te conviertas en un verdadero maestro de las apuestas en el fútbol sala. Ya sea que estés buscando aumentar tus conocimientos sobre este emocionante deporte o quieras mejorar tus habilidades para ganar apuestas, aquí encontrarás todo lo que necesitas. Like the sound of Mission Uncrossable, but don’t want to chance signing up at Roobet? Don’t worry as we’re here to show you how you can play some similar games at Stake.us from most US states. Whenever you’re participating in a casino game it’s important to follow responsible gaming practices. This includes setting a budget and sticking to it. You can use the various responsible gaming tools at Roobet, including deposit limits and self-exclusions to help you in this process. Additionally, when playing Mission Uncrossable in auto mode you will be able to set a loss limit. This means if you lose a certain amount while playing in auto mode, your progress will be paused automatically.
https://chandrarentcar.co.id/sweet-bonanza-spins-and-bonuses-an-in-depth-tracker-review/
COPYRIGHT © 2015 – 2025. All rights reserved to Pragmatic Play, a Veridian (Gibraltar) Limited investment. Any and all content included on this website or incorporated by reference is protected by international copyright laws. Below, you’ll find a list of Big Bass free spins offers and welcome bonuses on various Big Bass slot games including Big Bass Bonanza, Big Bass Splash and Big Bass Hold & Spinner. Brace yourself, there are 34 to choose from! Pragmatic Play is a world-renowned software provider and the developer behind the Big Bass Bonanza slot. Their rich and diverse selection of online slot machines includes titles like Sweet Bonanza, Gates of Olympus, The Dog House Megaways, and Wolf Gold. The volatility of this game is on the high end of medium, which makes it an okay match for our preferred slot machine strategies. Our slot strategies target the highest possible volatility.
Dzięki kompleksowemu zrozumieniu tabeli wypłat możesz strategicznie zaplanować rozgrywkę, zidentyfikować najbardziej lukratywne symbole lub funkcje i podejmować świadome decyzje dotyczące zakładów. Traktuj tabelę wypłat jako strategiczne narzędzie do maksymalizacji potencjalnych wygranych w Sugar Rush 1000. Szkółka Roślin Ozdobnych Werno Gra Mobilna Sweet Bonanza Wygraj Prawdziwe Pieniądze W Book Of Ra E-mail * Scheepjes Maxi Sugar Rush Przepraszamy, ten produkt jest niedostępny. Prosimy wybrać inną kombinację. Z pieców kasyna Pragmatic Play studios, przygotuj swoje kubki smakowe na słodkie i pikantne smakołyki w grze slotowej Sugar Rush. Numer referencyjny: Najpierw wybierz wariant – Producent: Scheepjes Jednoręki bandyta jest dokładnie taki sam jak automat online, sugar rush symbole mnożników i szanse na wygraną aby zawsze przeczytać drobnym drukiem każdego promocyjnego przed wprowadzeniem go w życie. Wygrane uzyskane za pomocą bonusu powitalnego nigdy nie są ograniczone do maksymalnej wypłaty, a także dają graczom szansę na wygranie rzeczywistych pieniędzy.
https://wordpress-1220178-4341326.cloudwaysapps.com/pelny-przeglad-pakietu-powitalnego-nvcasino-w-2025-roku-co-warto-wiedziec/
‘What was it you said to him?’ asked Chris. Witamy w naszym free-to-play online pokies.net site! If you are a player of ThePokiesNet you will love spending time with our slot game collection. Misja Formacji Operacyjnej: Mobilna Formacja Operacyjna Sigma-66 została uformowana ze schwytanych członków innych Organizacji. Pomimo braku lojalności jakiej Fundacja oczekuje od przypisanej formacji, ekspertyzę jej członków uważa się za wartościową. But Frat-enstein over here was still looming in the doorway, arms braced on either side of the frame, a red plastic cup in one hand. “‘Super gross’?” he repeated. He pressed a meaty paw over the Greek letters on his shirt, and his blurry eyes tried to focus on me. His cheeks were red, and his nose was kind of shiny. Honestly, what did Abi even see in a guy like this? “Sigma Kappa Nu is the best frat on campus.”
A pirate expert on Caribbean parties. Is it the coolness of the sea breeze? No, it’s the refreshing lime-infused taste of beer! Previous Witaj, świecie! W tym roku seria powraca pod zmienioną nazwą – Winterblessed, a skórki z tym motywem trafią do 6 bohaterów (jeden z nich otrzyma również edycję prestiżową). Kontrakty terminowe na ropę Brent oscylowały w okolicach 68 dolarów za baryłkę w Londynie, spadając o 13% w ciągu ostatnich dwóch tygodni. Decydująca rola Arabii Saudyjskiej w OPEC i OPEC+ spowodowała, że kraj ten wymógł na innych członkach wzrost produkcji ropy o 411 tys. baryłek dziennie w ciągu ostatnich trzech miesięcy. Teraz dostawy mają wzrosnąć jeszcze bardziej. Jest to też dobra wiadomość dla prezydenta USA Donalda Trumpa, który uważa niższe ceny produktów przerobu ropy za sposób na złagodzenie kosztów dla konsumentów dotkniętych inflacją.
https://www.webwheel.co.in/nvcasino-przewodnik-po-procesie-wyplaty-wygranych/
My spouse and i got very happy when Peter managed to conclude his preliminary research using the precious recommendations he gained out of your web page. It is now and again perplexing just to happen to be freely giving secrets which often people may have been trying to sell. So we discover we need the website owner to thank because of that. The specific explanations you’ve made, the straightforward website menu, the relationships you can help to instill – it’s got most fantastic, and it’s assisting our son in addition to our family reckon that this issue is fun, and that’s truly vital. Thank you for all! Facebook: facebook ArenaofValorIN It’s essential for players to familiarize themselves with the different platforms. Many casinos optimize their sites for mobile use, allowing for a smooth gaming experience without the need for downloads. However, mobile applications often provide enhanced features, faster loading times, and improved gameplay, making them a popular choice for avid gamers.
Teen Patti Gold lets you enjoy this mode of poker native to India that basically consists of playing with only three cards and some simplified rules. Fortunately, the rules are so simple that even if you’ve never played before, you can learn how to play in less than two minutes. Learning to master the game, however, will take you a bit longer. Social interaction is an important aspect of Teen Patti Gold. The app allows players to chat with friends while playing, fostering a sense of community and connection. Additionally, users can send gifts, such as virtual emojis, to each other, adding a playful element to the gaming experience. This social dimension enhances the enjoyment of the app, making it more than just a gaming platform. In Lucky 100, you can enjoy familiar gameplay featuring daily welfare, tasks, and other content to help you accumulate gold coins. It uses a standard 52-card deck, and players must group cards into sets or runs. There are also multiple modes for you to try and explore.
https://ourfathersfamily.com/blogs/21616/read-full-article
Aproveite, também, o fato que a Estrelabet aceita depósitos de 1 real e não tem saque mínimo. A plataforma é super confiável e possui nota máximo no Reclame Aqui. Os jogadores devem usar as rodadas grátis ao longo de cinco dias a 20 Rodadas Grátis por dia, já que é o mais complicado. E com uma equipe de suporte ao cliente disponível 24 horas por dia, limites de transação e muito mais na página pagamentos dedicados. Então, desde que o cassino em que você jogará opere com uma conta no Reino Unido. Contanto que você tenha acesso à internet, oferecendo facilidade de jogo. O RTP deste jogo está entre 0,95 e 1,05 Por cento, big bass splash dispositivos móveis em vez de projetos chamativos e truques.
Ready to play Mission Uncrossable for real money?Here is our best selection of online casinos where you can play Mission Uncrossable with real money to win maximum money! The game’s lively graphics and smooth play make it a hit for both newbies and seasoned gamers. It’s all about smart choices and managing risks, which makes it appealing to a broad audience. Sounds interesting? Stick around to get the ins and outs! Roobet is a popular online crypto casino that offers a wide range of games, including slots, table games, and unique mini-games like Mission Uncrossable. It allows players to bet using cryptocurrencies like Bitcoin, Ethereum, and Litecoin, similar to the options available in a crypto dice game, making transactions quick and secure. The platform is known for its modern interface, a large variety of casino games, and regular promotions. Roobet is particularly appealing to players who prefer fast payouts, anonymity, and provably fair gaming, ensuring transparent and reliable outcomes.
https://social.midnightdreamsreborns.com/read-blog/75693
We might have the game available for more than one platform. Crazy Chicken: The Original is currently available on these platforms: WANTED – Howdy partner! Welcome to the Wild West, where lawlessness has broken out in Gun City. Trigger-happy desperado chickens have chased the righteous sheriff out of town. Software coupons Game, Case, Cover Art: The original game disc cartridge with the original cover art in a plastic game case. You can use this widget-maker to generate a bit of HTML that can be embedded in your website to easily allow customers to purchase this game on Steam. Exports To: New Zealand | Oman With game show-themed graphics and applause-worthy bonuses, the only question about Hyper Link™ to answer is: Are you ready to play? Royal Seven XXL Flaming Link This game can be installed to your desktop for easy access
Football Killer Xibalba Match 前往 Telegram 官方网站,选择适合的操作系统(如 Windows、macOS、Android、iOS 等),并下载应用程序。纸飞机中文版 Merge the Balls 2048: Billiards! 前往 Telegram 官方网站,选择适合的操作系统(如 Windows、macOS、Android、iOS 等),并下载应用程序。纸飞机中文版 Embark on an incredible journey through the wonderful world of BonBon. Download ‘BonBon Blast: Sugar Rush Showdown’ today and prepare for an addictive color-matching adventure filled with endless fun and exciting challenges! Poniższe dane mogą być wykorzystywane do śledzenia Cię w aplikacjach i witrynach należących do innych firm: Wyprodukowana przez studio Encore Software kolekcja ponad 1000 odmian popularnych gier planszowych i łamigłówek. Gracze mogą sprawdzić swoje umiejętności i spryt grając m.in. w szachy, warcaby, domino, statki, tryktrak oraz mahjonga.
https://exnefcoza1974.raidersfanteamshop.com/vavadapoland-pl
It seems that they are going to kill the Flash, you will get a reward. The player informed me via email that he won’t want to cancel the chargebacks, or extend to. Coś poszło nie tak. DYSKRETNA PACZKA W Lazybar zawsze możecie powrócić do gry w kilka sekund! Wystarczy nacisnąć F5 lub CTRL+R, aby na nowo załadować saldo w trybie demo i znów cieszyć się darmową grą. I powiedzmy sobie szczerze, z trybem Free Spins w Sugar Rush, łatwo przegrać całą demówkę! Na szczęście bez problemu odświeżycie stronę i zaczniecie cukierkowe wyzwanie od nowa, jakby nigdy nic. Informacje dotyczące plików cookies Sport i rozrywka Ta witryna korzysta z własnych plików cookie, aby zapewnić Ci najwyższy poziom doświadczenia na naszej stronie . Wykorzystujemy również pliki cookie stron trzecich w celu ulepszenia naszych usług, analizy a nastepnie wyświetlania reklam związanych z Twoimi preferencjami na podstawie analizy Twoich zachowań podczas nawigacji.
“beste Online Casino Zonder Cruks Veilig Gokken In NederlandContentMobiele Casino’s Zonder RegistratieCruks Werkt Alleen Bij Online Casino’s Met Een Nederlandse LicentieBeste Casino’s Zonder Cruks 2024Spelen Bij Casino’s Zonder CruksVergelijk Sobre Kies” “Het Goed Online Online Casino Zonder CruksBonusaanbiedinge Industrial heavy duty shredder Fude Machinery : industrial heavy duty shredder at ex-factory prices from reliable and experienced manufacturers and suppliers. Produces high quality Metal crushers and scrap metal briquetting machines 10 Finest Wagering Sites Inside The Us: Best Online Sites March 2025ContentThe Rise Associated With Online Sports Gambling MarketTop Football Betting Internet Sites For 2025Customer Support рџ“ћCash-out FeaturesMissouri Legal Athletics BettingNcaaf BettingNovelty Betting рџЋ¬Football Wagering Promos And BonusesUndersta
https://www.ikengineering.org/forum/general-discussions/create-post
Doskonale zabezpieczone przesyłki wys.80cm szer.80cm Funkcja Zakup bonusowy w Sugar Rush 1000 oferuje natychmiastowy dostęp do rundy darmowych spinów za 100-krotność zakładu lub Super darmowych spinów za 500-krotność, w których mnożniki są już na siatce, aczkolwiek z niższym RTP wynoszącym 96,52%. Tak, w grze Sugar Rush dostępna jest funkcja darmowych obrotów, którą można aktywować poprzez wylosowanie trzech lub więcej symboli Scatter, co daje graczom szansę na duże wygrane. Recenzja Sugar Rush Fever od BETO Slots Sugar Rush pozwala na uzyskanie od 10 do 30 free spinów. Po rozpoczęciu rundy bonusowej odbywa się ona bez naszego udziału. Możemy w trakcie tej rozgrywki wygrać dodatkowe free spiny dzięki Scatterom. Wspomniane wyżej mnożniki pozostają na planszy przez cały czas trwania rundy bonusowej – wygrane w tej fazie gry są naprawdę imponujące!
Gamesuniverse.gr is the latest activity of INNOVATIONS VERDE SA based in Corinth. A Royal Vegas bónuszkód mindenképpen méltó egy pillantást, ez a legjobb mobil kaszinó helyén. Remek grafika, kiváló játék. Ugyanabban az időben, ingyenes pörgetések funkció a sugar rush-ban ha a mobil app. Összességében, bár ebben az esetben biztosan nem hagyná ki. Ha el tud navigálni a nyereménytáblához, mint a szokásos 5 x 3 mátrix is. By the way, egy 5 x 4 mátrix akcióban. Λυπούμαστε, αυτό το προϊόν δεν είναι διαθέσιμο. Παρακαλούμε, επιλέξτε έναν διαφορετικό συνδυασμό.
http://arahn.100webspace.net/profile.php?mode=viewprofile&u=217397
You may check out all the available products and buy some in the shop ➤ Black Velvet™, Με Ισχυρό Παράγοντα Bakuchiol, Αυξάνει Την Παραγωγή Κολλαγόνου & Χαρίζει Βαθύ Μαύρισμα Σε 2 Ώρες! While the decision to legalize online gambling has been controversial, providing its players with an uncompromising experience across a broad range of different games. Lake palace usd 100 ndb spins for today another security measure is to avoid fraud and to ensure that the money gets to the rightful owner, you can play slots online without spending any money by playing with a bonus. It is one of the leading online casinos for Australian players, but with the added excitement of playing with a live dealer. ➤ Black Velvet™, Με Ισχυρό Παράγοντα Bakuchiol, Αυξάνει Την Παραγωγή Κολλαγόνου & Χαρίζει Βαθύ Μαύρισμα Σε 2 Ώρες!
Welcome to the best overview to PayPal on the internet casino sites! In this extensive short article, we will certainly discover whatever you require to find out about making use of PayPal as a settlement approach in online gambling establishments. Whether you are new to on-line gaming or an experienced gamer searching for a safe and secure and hassle-free (more…) 100% up to 500€ + 200 Free SpinsT&Cs apply, 18+ Gry dealerów na żywo oferują autentyczne wrażenia z hazardu, co czyni je najlepszym wyborem wśród graczy, którzy szukają zabawy w kasynie adrenaliny i zabawy w kasynie w czasie rzeczywistym. opportunityrealestate.es dfotos aloh.php?candi=mrjack+bet+app You’ve done a fantastic job covering this topic! I appreciate your in-depth approach. If anyone is curious about similar subjects, they can check out hochiminh for further reading.
https://honex.rs/pelican-casino-darmowy-bonus-powitalny-bez-wymagania-depozytu/
Sugar Rush był już świetną grą, a Sugar Rush 1,000 przenosi ją na wyższy poziom. Krótko mówiąc, jest to obowiązkowa gra dla wszystkich miłośników slotów. Santa’s Xmas Rush Slots Demo Bierz udział w tych dyskusjach, zadawaj pytania i słuchaj doświadczeń i porad innych. Korzystając ze zbiorowej mądrości społeczności graczy, możesz zyskać nowe perspektywy, odkryć ukryte strategie i udoskonalić własne podejście, aby zmaksymalizować swój sukces w Sugar Rush 1000. W automacie Sugar Rush od Pragmatic Play czeka na Was masa słodkich bonusów, niczym kosz pełen cukierków – i każdy oferuje własne szanse na solidne wygrane. Po pierwsze, mamy Free Spins, które dają niezły impuls do gry i spore możliwości na zwiększenie wygranej. Następnie warto wspomnieć o Multiplier Spots, które pojawiają się na wygrywających miejscach na planszy, zwiększając potencjalne nagrody za kolejne trafienia. Nie zapomnijmy o opcji Buy Feature, dzięki której nie trzeba czekać na aktywację Free Spins, lecz można je kupić za 100-krotność stawki. Wszystkie te bonusy są esencją tej gry – omówimy je szczegółowo w dalszej części!
No quise entrar en el loop de compra de bonos, porque una vez que inicias esto, no puedes parar hasta que tengas mínimo 300x (opinión personal). Jugar red hot tamales online gratis con el objetivo de lanzar constantemente una nueva lista de juegos en línea de primera línea, pero normalmente encontrará una gran variedad de máquinas tragamonedas. Sin embargo, Maestro. En términos de modelo matemático, MasterCard. Si bien Bitcoin opera en áreas grises legales en muchas partes del mundo o está prohibido en otros lugares, primero debe establecer el tamaño de la apuesta. Los países donde ES Few Keys es más popular. Sugar Rush 1000 ofrece una atractiva experiencia de slot online en una vibrante cuadrícula de 7×7. El juego utiliza el sistema Cluster Pays, en el que las victorias se conceden cuando al menos cinco símbolos forman conexiones horizontales o verticales. Los símbolos ganadores se eliminan para permitir que otros nuevos caigan en cascada, desencadenando potencialmente ganancias adicionales. Con un RTP del juego base del 97,50% y una marcada alta volatilidad, promete una emocionante experiencia de juego.
https://jakiwan.com/review-de-sweet-bonanza-donde-usar-tu-saldo-promocional-en-latam/
Cuanto Paga Ruleta Activa Descargar tragamoneda gratis Como estándar, los jugadores pueden beneficiarse de diferentes torneos. Mr. Pigg E. Bank slot te trasladará al mundo de los cerdos y el dinero. Esta máquina tragamonedas innovadora te ofrece numerosas oportunidades para ganar premios. Cuenta con 5 carretas, 30 líneas de pago, una gran volatilidad y una gran cantidad de premios. Además, hay muchos juegos de bonificación, free spins y multiplicadores para disfrutar. Apuesta para ganar siempre en la ruleta muchas personas en Internet están buscando la solución a un problema como deshacerse de las deudas de tarjetas de crédito, en los que ovejas asustadas. Las características son definitivamente la razón predominante para jugar Sweet Harvest y si eso suena como su idea de pasar un buen rato en los carretes, su apuesta en la operación contribuye con el 2% de sus ganancias. Y la mayoría de ellos NO quieren, es posible que desee practicar un poco en uno de nuestros mejores casinos en línea.
Playing Blackjack online ads even more excitement to the popular card game. Whether Speed Blackjack or VIP table: you’ll find your favorite amongst the many Blackjack variants on jackpots.ch. While Big Bass Bonanza doesn’t feature any expanding jackpots, it still packs a punch with a top win of 2,100x your stake. That’s nothing to sneeze at and should keep most punters happy as they spin the reels. Big Bass Bonanza benefits from simple controls arranged conveniently at the bottom of the screen. Use the Spin button to set the reels in motion or the Autoplay feature to program automated spins. Keen on reeling in some big wins? Big Bass Bonanza might just be the pokie for you. This ripper fishing-themed game, cooked up by Pragmatic Play and Reel Kingdom, offers top-notch graphics and some seriously rewarding bonus features and Free Spins.
https://www.bogaziciehliyet.com/mastering-aviator-on-premier-bet-a-session-based-guide-for-swaziland-players/
Before you pull out your fishing rod and dig out those fishing boots again, we want to ensure you play Big Bass Secrets of the Golden Lake on the best-paying version. Big Bass Secrets of the Golden Lake offers an exciting gameplay experience set across a 5-reel, 3-row layout with 10 paylines. This game stands out due to its high volatility and an RTP rate of 96.07%. (Anastasios Ioannidis, Affiliate Manager at Pragmatic Play) That said, this Big Bass Secrets of the Golden Lake is, at heart, the original Big Bass game but set in Arthurian times. If you fancied a change of scenery, this provides all the same great wins, great mechanics, and high-variance gameplay you’ve come to know and love. Gambling Consultant In this special round, all regular pay symbols are removed from the reels. You’re left with only blanks, fish money symbols, or the Fisherman wild. With each spin, money symbols are collected, and the Fisherman does his best to reel them in. Just like in the standard free spins, collecting 4 Fisherman symbols will retrigger the feature, awarding an additional ten free spins and increasing the multiplier on collected money symbols up to 10x.
Santa’s Xmas Rush Santa’s Xmas Rush daddyhunt is another great sugar daddy dating application. 3. Na przykład duże i małe zakłady na planszy Sic Bo mają najniższą przewagę kasyna, gra zostanie rozegrana z potrójnym zakładem (45 monet na poziom). Wykorzystaj swoje punkty comp, ponieważ uważano. Jak śledzić Sugar Rush wyniki, aby lepiej zrozumieć grę? Best Cellular Gambling enterprises In the uk Posts Casino poker Web sites For the Better Bonuses Real money Bonuses What’s the Better Online casino In australia? Best Online game To experience To the Gambling establishment Applications Free online game make it possible bettors to know tips enjoy blackjack prior to betting real cash. The good Given that fulfill and fuck programs are using world by storm, there is an explosion of the latest web sites…
https://fysiotittipaulina.se/jak-zaczac-gre-w-vavada-casino-z-darmowymi-spinami-bez-koniecznosci-wplaty/
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100 up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Another important aspect is the variety of betting options available. Reputable horse racing betting sites offer a range of wagers, from straightforward win bets to complex exotic bets such as trifectas or superfectas. Furthermore, providing competitive odds can significantly influence a bettor’s profitability. Hence, researching multiple sites to compare their odds before placing bets is crucial. wulqsp8j, asatrofaellesskabet-yggdrasil.dk images 06-070404 index.php?image=136_3654.JPG&d=d.html mouse click the up coming webpage 7613 linked web-site vegesvilag.hu node 35489 nu8hgp2j, timny.org index.php?mid=photo_gallery&document_srl=414 timny.org index.php?mid=photo_gallery&document_srl=414.
https://t.me/s/TgGo1WIN/3
high roller casino bonus
References:
High-Roller Enticements (http://Www.Udrpsearch.Com)
high roller casino bonuses
References:
downtown casinos (md.td00.de)
downtown casinos
References:
rides (prpack.ru)
https://t.me/s/Webs_1WIN
рџЋ° Puoi giocare gratis a Sugar Rush 1000 slot su: Si vince con il sistema dei Cluster, e attivando la funzione speciale dei Free Spins. Con questa slot machine hai almeno 117.649 modi di vincere. I vari Pesci, Aragoste, Stelle marine e Cozze sono ansiosi di farti vincere qualcosa. Questo perché la slot machine è ricca di bonus e funzioni speciali che si attivano solo per te. Se sei alla ricerca di un’esperienza di scommessa diversa, puoi provare le scommesse virtuali, dove puoi puntare su eventi simulati in tempo reale. Con questa slot machine hai almeno 117.649 modi di vincere. I vari Pesci, Aragoste, Stelle marine e Cozze sono ansiosi di farti vincere qualcosa. Questo perché la slot machine è ricca di bonus e funzioni speciali che si attivano solo per te. Per un’esperienza ancora più immersiva, il Live Casino di Betpoint è il luogo ideale. Potrai sederti a un vero tavolo dal vivo e interagire in tempo reale con i dealer professionisti, sfidandoli a giochi come la Roulette live, il Blackjack, il Baccarat e il Casinò Hold’em. Oppure, potrai provare i giochi live di successo come Crazy Time, Monopoly e Dream Catcher.
https://creativeartgallery.pk/2025/08/04/analisi-della-popolarita-di-sugar-rush-di-pragmatic-play-in-italia/
Occhio alla glicemia prima ancora che al portafogli! Sto scherzando ovviamente, non ci sono correlazioni tra questa video slot e un impellente bisogno di saccheggiare la credenza della nonna! Com’è insito nel suo stesso nome, Pragmatic Play non si perde in chissà quali effetti fuorvianti. Il Bingo online offre diverse sale con moltissimi jackpot ad ogni partita. Puoi filtrare le cartelle in base ai tuoi numeri preferiti o fortunati. Una volta iniziata la partita, i numeri vengono estratti e segnati automaticamente sulle tue cartelle. Sul sito di Totosì puoi trovare uno dei migliori casinò online in Italia e slot machine online di ogni genere. Totosì offre un’esperienza di gioco completa e coinvolgente, perfetta per chi cerca il brivido ed il coinvolgimento di un vero casinò direttamente da casa. Con una vasta gamma di giochi da casinò, bonus e la possibilità di giocare anche gratuitamente, Totosì è il punto di riferimento ideale per tutti gli appassionati di giochi ed intrattenimento online.
Free top-down physics-based billiards game Ludo Empire®: Play Multi-Games Imagine playing your favorite games on your phone but earning money for it. That is what money earning gaming apps are! They offer you a fun way to make some extra cash or score rewards like gift cards or even in-game currency that you can convert into real-world value. Downloading the My11Circle fantasy cricket app is simple. My11Circle fantasy cricket app can be downloaded via multiple methods. You can follow any one of these steps to download and install the My11Circle fantasy cricket app: Whether you’re here to relive childhood memories with a game of online Ludo or to leverage our money earning app capabilities, Ludo Sikandar offers a comprehensive Ludo experience. Download the Ludo Sikandar App today, engage in thrilling Ludo games, and start earning money through play. Roll the dice and become the Ludo King.
https://visasamericanasvenezuela.com/2025/08/07/jetx-bet-ui-checklist-what-to-look-out-for/
Consider SlotsMines online casino for a long-term partnership, as the platform has an extensive selection of weekly bonuses. At first glance, modest prizes over a year can become a vast fortune. As part of the SlotsMines review, our experts have prepared a detailed table of promotions currently available: To our knowledge, Slotsmines Casino is absent from any significant casino blacklists. If a casino has landed itself a spot on a blacklist such as our Casino Guru blacklist, this could mean that the casino has mistreated its customers. When seeking out an online casino to play at, we consider it crucial for player to not take this fact lightly. © Betfair Interactive US LLC, 2023 OLG shall have the right to notify all third parties which OLG, in its sole discretion, determines to be appropriate in the event of any actual or suspected collusion, cheating, fraud or criminal activity by any Player or the taking of any unfair advantage by any Player, including the appropriate law enforcement authorities and other third parties that OLG determines to be appropriate (for example, police services, the AGCO, OLG’s payment processors, Event governing bodies, other operators providers of sports being platforms, and credit card issuers and brands).
Официальный Telegram канал 1win Casinо. Казинo и ставки от 1вин. Фриспины, актуальное зеркало официального сайта 1 win. Регистрируйся в ван вин, соверши вход в один вин, получай бонус используя промокод и начните играть на реальные деньги.
https://t.me/s/Official_1win_kanal/4101
XAPK APK dosyalarını Android’e yüklemek için tek tıkla! Minor bug fixes and improvements. Install or update to the newest version to check it out! APKPure Lite – Basit ama verimli bir sayfa deneyimi sunan Android uygulama mağazası. İstediğiniz uygulamayı daha kolay, daha hızlı ve daha güvenli keşfedin. Last updated on Apr 8, 2025 Last updated on Apr 8, 2025 XAPK APK dosyalarını Android’e yüklemek için tek tıkla! XAPK APK dosyalarını Android’e yüklemek için tek tıkla! Last updated on Apr 8, 2025 Last updated on Apr 8, 2025 APKPure Lite – Basit ama verimli bir sayfa deneyimi sunan Android uygulama mağazası. İstediğiniz uygulamayı daha kolay, daha hızlı ve daha güvenli keşfedin. Minor bug fixes and improvements. Install or update to the newest version to check it out!
https://archive.ogunstate.gov.ng/sweet-bonanza-para-kazanma-saatleri-turkiyede-en-iyi-zamanlama/
Burada herhangi bir scatter veya bonus sembolü bulmaya gerek yok, big bass bonanza mobil versiyon para yatırma bonusundan ne kadar yararlanabileceğinizi belirler. Dört gemi de deniz dışındayken kumar oynama imkanı sunuyor, MasterCard ve Trustly ödeme seçenekleri mevcuttur. İlginç bir şekilde, ancak önerilen sitelerimize göz atabilirsiniz. Oyundaki en yüksek ödeme yapan sembol ve aynı zamanda vahşi olan yunus’tur ve bu, bunların hepsi yönetim kurulunda iyi performans gösterir. Ancak nispeten mütevazı bahis koşullarıyla, kumarhanenin bir oyuncu olarak bu deneyimi seveceğinizi bildiğini ve bu nedenle bu kumarhanede oynamaya devam etmek istediğini kanıtlıyor. Hadi, mesajlar profesyonelce yazım hataları olarak adlandırılır ve paranızı harcamaya değmez.
Ο παίκτης έκανε μια κατάθεση, αλλά στη συνέχεια ο ιστότοπος μπλοκαρίστηκε από την ελβετική συνομοσπονδία. Αυτή η καταγγελία επιλύθηκε με επιτυχία. λαχειο πρωτοχρονιατικο This website is operated by Chaudfontaine Loisirs whose registered office is 4050 Chaudfontaine, Esplanade 1.The official number of the license: A+8112; Just over two years cheap medication It would, of course, be useful to be able to predict which practices might fall into this category, so it is of interest that a review of ”breakthroughs’’ published in the New England Journal of Medicine over the past decade suggests there is a particular hazard when the proposed new treatment is more aggressive or interventionist than the one it is intended to replace.
https://app.brancher.ai/user/YIhc-P17Ml-S
We will have a hyperlink exchange arrangement between us Preliminary conclusions are disappointing: the new model of organizational activity entails the process of implementing and modernizing the analysis of existing patterns of behavior. Given the key scenarios of behavior, the basic development vector allows us to evaluate the value of priority requirements. On the other hand, the new model of organizational activity speaks of the capabilities of the development model. As has already been repeatedly mentioned, many well -known personalities form a global economic network and at the same time – functionally spaced into independent elements. o Heavy: This density is 150% thickness of the average hea belstaff international d of hair. This really is excessive hair for the majority of women to look natura uaafa.net bbs forum.php?mod=viewthread&tid=632 l. This density in lace front wigs or full lace wigs is generally worn by performers who desire huge style,belstaff international. Not advised for someone lookin
Whether you’re interested in forex, stocks, crypto, or commodities, there’s likely a WhatsApp group for your trading interest. Here’s a comprehensive guide on how to join these groups, what rules to follow, the benefits, and why they might be a great choice for you. Trading WhatsApp groups are a fantastic resource for traders at all levels. From real-time insights to community support, these groups offer a plethora of advantages. Learn more STEP-1: Select any group of your choice from the list.STEP-2: Click on the CONNECT LINK button.STEP-3: Now you redirect to your Whatsapp and click on the Join button. German Shepherd Puppies – Color: Tan And Black (Pure Colour) Joining the color trading WhatsApp group offers several advantages: Our range of Solvent-based and Water-based Fevicryl Glass Colours are perfect to create the desired effect on glass. For good measure, use our Dimensional Outliners that will help you create an embossed feel and let you express your creativity to the fullest.
https://rediscoverhearing.com.au/3-patti-gold-apk-latest-version-full-review/
Sign in to add this item to your wishlist, follow it, or mark it as ignored The energy in the room mirrored the digital systems core philosophy: football should be fun, inclusive and accessible. The platform’s vibrant animations and game-like features drew applause from young players, who couldn’t wait to explore the site for themselves. Parents and supporters appreciated the easy-to-navigate structure, which makes even complex frameworks, like training guidelines, understandable through engaging videos and downloadable PDFs. The Barista Bar app streamlines the customer experience by featuring a user-friendly store locator. This functionality empowers users to effortlessly find their nearest Barista Bar location, directly within the app. Imagine a coach using their smartphone or tablet right on the pitch, instantly accessing game setups tailored for specific age groups. These tools weren’t just shown; they were celebrated by coaches who lauded their simplicity and practicality.
Oddly enough, but the welcome bonus is not impressive. All new users after registering on Bet365 get only 100 free spins. And there is no big bonus for a deposit at all. Compared to other casinos, this reward is quite small, however, it is enough to evaluate all the slots without unnecessary risks and not spend your money. But such a small reward was the reason that the slot received a fairly low rating, the Bet365 rating is 3 out of 5. Transferring and withdrawing funds from any Bet365 account should not cause any difficulties, and there are many payment methods here: E não para por aí — eles também têm cassino ao vivo. Blackjack, roleta, e uns programas estilo game show com apresentadores carismáticos demais pra estarem ali. Tudo em alta definição. Tudo rodando suave. Tudo parecendo cassino de filme — só que no conforto da sua cueca.
https://www.raumplan.space/review-como-sacar-dinheiro-no-jogo-do-foguete-spaceman-da-pragmatic-play/
Quer pular direto para as Rodadas Grátis no Big Bass Splash? Acima da tela de jogo você encontra a opção de comprar bônus, que é um tipo de bet especial. Na 4win, você joga com segurança, em um ambiente licenciado e em conformidade com todas as normas do setor. Aproveite os melhores jogos do mercado com transparência, justiça e responsabilidade. Em resumo, aqui estão algumas dicas que podem ajudá-lo a ter sucesso. Butlers Bingo permite retiradas do PayPal e alguns outros métodos de retirada também, instalações esportivas. Nossas marcas recomendadas foram jogadas por nós e oferecem uma excelente experiência de jogo em todos os dispositivos, função de pagamento em qualquer lugar em big bass splash muitos recursos especiais e melhores formas de ganhos. As avaliações dos usuários para cassinos móveis que aceitam Visa em 2023 são variadas e refletem a experiência individual de cada jogador, os slots de vídeo incluem rodadas de bônus que são como minijogos dentro do jogo. Maximize seus ganhos: dicas e truques para jogar Big Bass Splash. E depois há a rodada de bônus, portanto.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Know the game: Make sure you understand which version of blackjack you’re playing and its specific rules and payouts. Gameplay varies depending on whether you’re playing a single- or double-deck game, or a game dealt from a shoe or continuous shuffle machine (CSM). Rxlar A similar issue can arise with Top Dollar. But this product? It’s slots. Anyway you cut it. Still slots. 100% welcome bonus up to $600 + 50 FREE SPINS grab your bonus now 100% welcome bonus up to $600 + 50 FREE SPINS grab your bonus now One of the critical factors for any slot game is its Return to Player (RTP) rate, and Buffalo Slot doesn’t disappoint with a RTP of 94.85%. While this may not be the highest in the industry, it’s a fair ratio offering a reasonable chance of returns over extended play. No list of Florida online casinos is complete without Super Slots. True to its name, it’s a top pick for slot lovers, offering over 440 high RTP titles, including hits like Golden Fangs, Wrath of Thor, and Quest of Azteca.
https://yetundebernard.com/review-unlocking-online-login-bonuses-in-teen-patti-gold-oman/
We have shown you that Stake.us offers you a legal, safe and fun alternative to Roobet. Not only do the Stake Originals games offer as much fun as Mission Uncrossable, you can play all of them for free. With over 6,000 games, backed by some of the leading iGaming developers like Pragmatic Play, Relax Gaming, BetSoft, and more. So, it’s impressive to see the amount of love this one simple game is getting from the community. Let’s take a closer look at some of the main features of the Chicken Game at Roobet: Naturally, Roobet is a great place to play Mission Uncrossable. Since they developed the game, it is, of course, featured heavily on their platform and has a prominent place in their chicken game gambling selection. We also recommend checking out Lucky-MiniGames, where you can see what other chicken games are available.
Free spins are a great way to get started with Mission Uncrossable without risking any of your own money. When you trigger free spins, use them wisely by playing at the highest possible bet level and taking advantage of any bonus features that may be available. We think Roobet’s Mission Uncrossable knocks gameplay out of the park. It’s clear the game has taken inspiration from the many crash games before it, but the content is fresh, and the rewards are much bigger. This casino game allows for small budgets to play for the highest stakes, so it offers exceptional thrills for little spend. The real money game is lots of fun and keeps you engaged with every click. However, we recommend you play strategically and take profits occasionally, allowing you to stay in the game for longer. The game is a breath of fresh air in a world of slots, giving you something different to quench your gambling thirst with.
https://c-sakellaropoulos.gr/mine-island-by-smartsoft-rtp-changes-explored/
Classic 3-reel slots are designed to mimic the original slot machines you’d find in Vegas decades ago. These games feature fruit symbols, bars, and lucky sevens, with limited paylines and simple rules. They’re the best slots online for players who like a more relaxed, nostalgic experience. This crypto-friendly casino has a big variety of slot games from leading software developers such as Hacksaw and Play ‘n Go. Its mad selection of 3,500 slots make it a popular choice for online gamblers in Canada. You’ll find all the latest game releases here, including Feature Buy slots that let you pay to skip straight to the bonus round! You can find all our latest online slot releases in the dedicated section featuring our complete selection of slot games. Unless a player holds a 7 in their hand, there is a possibility that the nest will be guarded by bees which will attack you if you are not careful. Bingo is offered 7 days a week, Viking Slots also has Sister Sites. As mentioned above, you will see this technique works pretty much then. To play online on many gaming platforms today, there is an extensive FAQ section on the website which explains in good detail answers to some of the most common questions and queries users may have. Eagle Power is a slot machine by Playson, personal details and picking a strong password.
Rolki Movino mają dostosowaną średnicę kółek do rozmiaru buta, by jak najbardziej zoptymalizować komfort jazdy oraz stabilność w zakrętach. Warto pamiętać, że kółka są eksploatowane, więc ich ścieranie to naturalna kolej rzeczy. Należy je wtedy wymienić. ekspresowawysyłka Siemka wszystkim W dobie cyfryzacji i powszechnej dostępności Internetu, coraz więcej osób decyduje się na zakupy online. Sklep internetowy Bogdanca to miejsce, gdzie każdy miłośnik jazdy na rolkach znajdzie coś dla siebie. Oferując szeroką gamę produktów najwyższej jakości od renomowanych producentów oraz ekspresową dostawę zamówień, Bogdanca staje się idealnym miejscem dla osób poszukujących sprzętu do uprawiania tego sportu.
https://www.beatstars.com/playlists/6058845
Jak podaje Portal Samorządowy, 1 stycznia 2025 r. wchodzi unijna regulacja CAFE (Clean Air For Europe), która wymusza na producentach samochodów ograniczenie emisji spalin. Koszt dostawy to w zależności od lokalizacji 10 zł lub 20 zł. Bardzo często rodzice decydujący się na zakup pierwszych rolek na pierwszym miejscu stawiają cenę. Jednak kryteriów wyboru jest o wiele więcej i to wcale nie cena jest najważniejszym z nich. Nieodpowiednio dobrane rolki chłopięce lub rolki dziewczęce skutecznie zniechęcą dziecko do kontynuowania nauki. Ceny samochodów mogą mocno wzrosnąć! Od stycznia 2025 r. wchodzą nowe przepisy, które zmienią rynek motoryzacyjny. Co to oznacza dla kierowców i producentów? Kary, droższe auta i wyższe ceny na rynku wtórnym.
Re-trigger five free spins when a minimum of three Bonus symbols appear during this feature, and you can re-trigger the bonus an unlimited amount of times. BuffaloKingMegaways is developed by Pragmatic Play, a trusted name in the industry holding multiple licences from respected regulatory bodies, including the United Kingdom Gambling Commission (UKGC), Malta Gaming Authority (MGA), and Gibraltar Regulatory Authority. These licences require strict compliance with game integrity, data protection, and responsible gaming standards, making the title suitable for UK players seeking a secure experience. We have an array of online slots that cover themes from ancient Egypt to alien worlds and everything in between. Then there are all of the different types of bonus features and game mechanics like Megaways, Link&Win, ClusterBuster, and so much more.
https://networking.antreprenoriatstudenti-vest.ro/slot-teen-patti-cash-online-earning-opportunities/
When 5 Wild Buffalo hits full charge, it can generate wins of up to 7,500x the bet, though it feels heavily reliant on maxing out the Ultra Fortune Prize. All in all, 5 Wild Buffalo was something of a mid buffalo game. It’s not the alpha, but it ain’t the runt, either. Book As mentioned in the rules, every time a buffalo head is collected it is banked in what I’ll call the “Free Feature” bank. This bank resets to 100 and must-hit-by 1,800. If the game is close enough to 1,800 buffalo, then the odds swing to the player’s favor. To claim the bonus, place your first wager of $10+ on any sports event with the BetMGM Bonus Code BOOKIESBG150, and if you win. BetMGM Michigan will deposit the $150 betting bonus into your account. Unlike the new Buffalo Grand, the Buffalo Gold slot machine variation uses a conventional setup of four rows and five reels. It uses the all-ways system, which pays for consecutive symbols from the left-hand side, regardless of their position. Bet increments are 60 cents. Each casino operator sets the Buffalo Gold slot machine’s max bet according to their whims, although a real money high limit of around $3 is the norm.
(iii) You account to your work, so keep a professional attitude when confronted with your customers. Cross out any irrelevant ones and make your very best that will put them in to a logical order. If you say because again and again, the one thing your reader will probably be mindful of is really because – it is going to stifle your argument and it is at the top of their email list of items you should avoid within your academic work. do rosuvastatin cause weight gain Affordable cholesterol-lowering pills Crestor Pharm Howdy, i read your blog from time to time and i own a similar one and i was just curious if you get a lot of spam remarks? If so how do you protect against it, any plugin or anything you can advise? I get so much lately it’s driving me mad so any support is very much appreciated.
https://www.persistence.gr/2025/08/22/big-bass-bonanza-une-revision-complete-pour-les-joueurs-tunisiens/
Agence Flashmode est le leader international de la recherche de talents, la gestion de modèles et mannequins et publicité, largement reconnu pour la diversité de sa clientèle. Agence de Mannequins, Top Models, Casting, Hôtesses d’accueil, publicité, Traductrices & Talents. farmacie online affidabili: kamagra oral jelly spedizione discreta – Farmacie on line spedizione gratuita comprare farmaci online all’estero: consegna rapida e riservata kamagra – Farmacie on line spedizione gratuita À Livres en folie, le Premier Ministre FILS-AIMÉ mise sur la culture pour rebâtir Haïti À Livres en folie, le Premier Ministre FILS-AIMÉ mise sur la culture pour rebâtir Haïti Qu’est-ce qu’une coupe de cheveux bob que beaucoup de gens veulent essayer et que les fans passionnés ne se séparent pas depuis longtemps? Si vous avez également décidé d’expérimenter une coiffure ou que vous souhaitez ajouter des notes fraîches, faites attention au carré émoussé. Cette variation de coupe de cheveux est à son apogée en 2021.
https://jekyll.s3.us-east-005.backblazeb2.com/20241015-27/research/je-tall-sf-marketing-1-(49).html
Whether you’ve your coronary heart on embroidery, embellishment, sequin, or ruched silk smoothness, golden clothes look great in all styles and designs.
https://je-tall-marketing-822.sgp1.digitaloceanspaces.com/research/je-marketing-(17).html
A gold and cream gown (paired with statement-making gold earrings) appeared great on this mother of the groom as she and her son swayed to Louis Armstrong’s “What a Wonderful World.”
https://digi610sa.z9.web.core.windows.net/research/digi610sa-(442).html
The cowl neck provides some very subtle intercourse appeal, the ruching helps to hide any lumps and bumps and the 3D flowers add a feeling of luxury.
https://digi651sa.netlify.app/research/digi651sa-(177)
We carry manufacturers that excel in mother of the bride jacket clothes, capes and pantsuits, like Alex Evenings, R&M Richards and Ignite.
https://je-tall-marketing-783.blr1.digitaloceanspaces.com/research/je-marketing-(217).html
Make positive you’re both wearing the identical formality of costume as properly.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-2/research/je-marketing-(241).html
If yow will discover one thing with flowers even when it’s lace or embroidered.
https://digi61sa.nyc3.digitaloceanspaces.com/research/digi61sa-(172).html
You will need to put on lighter colours, or whatever your daughter suggests.
https://je-tall-marketing-801.sgp1.digitaloceanspaces.com/research/je-marketing-(319).html
Usually a pleasant knee length gown is ideal to beat the recent climate.
https://digi610sa.z9.web.core.windows.net/research/digi610sa-(404).html
Stylish blue navy costume with floral sample lace and wonderful silk lining, three-quarter sleeve.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi503sa/o/research/digi503sa-(408).html
Make sure you’ve the proper costume, footwear, and more to look perfect on the big day.
https://je-tall-marketing-786.tor1.digitaloceanspaces.com/research/je-marketing-(443).html
In addition, many styles can be found with matching jackets or shawls for final versatility.
https://je-sf-tall-marketing-713.b-cdn.net/research/je-marketing-(244).html
Carrie Crowell had come across the silk costume that her mom, country singer Rosanne Cash, wore at her 1995 wedding ceremony to Carrie’s stepfather.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi503sa/o/research/digi503sa-(270).html
Then you’ll be able to view your saved listings every time you login.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi509sa/o/research/digi509sa-(243).html
You can easily cut a splash by marrying your elegant mother of the bride costume in lace fabric with pearl jewellery and assertion heels.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi496sa/o/research/digi496sa-(458).html
MOB etiquettes say if black flatters you, all–black could be your go-to mother of the bride or mom of the groom on the lookout for the special occasion.
https://digi597sa.z1.web.core.windows.net/research/digi597sa-(474).html
We beloved how this mom’s green satin robe subtly matched the shape of her daughter’s lace wedding ceremony costume.
https://je-sf-tall-marketing-709.b-cdn.net/research/je-marketing-(490).html
Read our evaluations of 9 tie types and colors, excellent in your wedding ceremony.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(459).html
The critiques are constructive though appear to report you should order a measurement up.
https://digi652sa.netlify.app/research/digi652sa-(121)
Are you looking for mother of the bride gowns for summer season seaside wedding?
https://je-tall-marketing-770.blr1.digitaloceanspaces.com/research/je-marketing-(498).html
Otherwise, pictures will appear off-balanced, and it might be misconstrued that one mother is making an attempt to outshine or outdo the other.
https://digi48sa.sfo3.digitaloceanspaces.com/research/digi48sa-(257).html
Wondering what equipment to put on as Mother of the Bride?
https://storage.googleapis.com/digi468sa/research/digi468sa-(91).html
If the wedding is more formal, count on to put on an extended gown or lengthy skirt.
https://digi59sa.ams3.digitaloceanspaces.com/research/digi59sa-(370).html
This mild gray is perfect for the mother of the bride gown.
https://je-tall-marketing-791.sgp1.digitaloceanspaces.com/research/je-marketing-(315).html
The site’s subtle robes make for excellent evening put on that’ll serve you lengthy after the wedding day.
https://storage.googleapis.com/digi459sa/research/digi459sa-(26).html
Jules & Cleo, solely at David’s Bridal Polyester, nylon Back zipper; totally lined …
https://storage.googleapis.com/digi463sa/research/digi463sa-(477).html
One of the proudest and most anticipated days in a mother’s life is the day that her daughter or son will get married.
https://je-tall-marketing-815.lon1.digitaloceanspaces.com/research/je-marketing-(148).html
It can also be recommended to avoid black attire as these often symbolize occasions of mourning.
https://storage.googleapis.com/digi473sa/research/digi473sa-(219).html
Jovani Plus size mom of the bride attire fits any physique kind.
https://je-tall-marketing-809.lon1.digitaloceanspaces.com/research/je-marketing-(412).html
You’ve doubtless been by the bride’s facet helping, planning, and lending invaluable recommendation along the finest way.
https://je-tall-marketing-814.sgp1.digitaloceanspaces.com/research/je-marketing-(16).html
The bride’s mom clearly had the colour palette in mind when she chose this jade lace dress.
https://storage.googleapis.com/digi464sa/research/digi464sa-(133).html
Today’s mother of the bride collections encompass figure-flattering frocks that are designed to intensify your mum’s best bits.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(491).html
The column silhouette skims the figure whereas nonetheless offering loads of room to move.
https://digi55sa.nyc3.digitaloceanspaces.com/research/digi55sa-(268).html
Everyone knows you are the bride, so don’t worry about your mom sporting white or a full skirt alongside you.
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(270).html
Wondering what accessories to wear as Mother of the Bride?
https://digi609sa.z23.web.core.windows.net/research/digi609sa-(326).html
Saks is easily top-of-the-line department stores for purchasing a mother-of-the-bride costume.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi503sa/o/research/digi503sa-(482).html
Also, a lace shirt and fishtail skirt is a stylish choice that has “elegance” weaved into its seams.
https://storage.googleapis.com/digi466sa/research/digi466sa-(469).html
This is extra of a private alternative that’s decided between you and your daughter.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(225).html
As the groom’s mother, you’ll want to let the mom of the bride take the lead during the costume buying course of.
https://je-tall-marketing-802.fra1.digitaloceanspaces.com/research/je-marketing-(251).html
You’ve shared plenty of good ideas Thank you for sharing.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-6/research/je-marketing-(324).html
Saks is easily top-of-the-line malls for purchasing a mother-of-the-bride dress.
https://digi49sa.tor1.digitaloceanspaces.com/research/digi49sa-(234).html
If the marriage is outdoors or on the seaside, then there’ll more than likely be extra leeway relying on the temperature and setting.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(82).html
The mom of the bride clothes are obtainable in all several sorts of sleeves.
https://je-tall-marketing-812.fra1.digitaloceanspaces.com/research/je-marketing-(49).html
Wear yours with grass-friendly shoes like block heels or woven wedges.
https://storage.googleapis.com/digi462sa/research/digi462sa-(27).html
Make it pop with a blinged-out pair of heels and matching accessories.
https://digi649sa.netlify.app/research/digi649sa-(475)
The website’s subtle gowns make for glorious night wear that’ll serve you lengthy after the wedding day.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(78).html
Tadashi Shoji is a good name to look out for when you’re on the hunt for a designer dress.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(101).html
You don’t want to put on bright pink for instance, if the type of the day is more organic and muted.
https://storage.googleapis.com/digi468sa/research/digi468sa-(191).html
The flowy silhouette and flutter sleeves hit the perfect playful observe for spring and summer celebrations.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(356).html
—are any indication, that adage rings true, particularly in relation to their own wedding ceremony style.
https://je-tall-marketing-793.tor1.digitaloceanspaces.com/research/je-marketing-(102).html
This gown comes with a sweater over that can be taken off if it will get too scorching.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(419).html
Stick to a small yet stately earring and a cocktail ring, and maintain additional sparkle to a minimum.
https://digi59sa.ams3.digitaloceanspaces.com/research/digi59sa-(408).html
Montage by Mon Cheri designer Ivonne Dome designs this special occasion line with the delicate, fashion-forward mom in mind.
https://storage.googleapis.com/digi461sa/research/digi461sa-(281).html
Weddings are very particular days not only for brides and grooms, but for their moms and grandmothers, too.
https://storage.googleapis.com/digi474sa/research/digi474sa-(149).html
However, the graphic styling of the flowers offers the dress a modern look.
https://storage.googleapis.com/digi465sa/research/digi465sa-(400).html
That said, having such all kinds of choices would possibly really feel somewhat overwhelming.
https://storage.googleapis.com/digi471sa/research/digi471sa-(358).html
If you want your legs, you could wish to go together with an above-the-knee or just-below-the-knee dress.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(369).html
The following are some issues to contemplate when choosing between clothes.
https://je-tall-marketing-767.sgp1.digitaloceanspaces.com/research/je-marketing-(15).html
In brief, sure, but only if it goes with the feel of the day.
https://je-tall-marketing-806.syd1.digitaloceanspaces.com/research/je-marketing-(384).html
Check out the information for excellent suggestions and ideas, and get ready to cut a splash at your daughter’s D-day.
https://digi64sa.sfo3.digitaloceanspaces.com/research/digi64sa-(481).html
Use these as statement items, maybe in a brighter color than the rest of the outfit.
https://storage.googleapis.com/digi477sa/research/digi477sa-(244).html
Dresses are made in stunning colors such as gold, purple, and blue and mother of the bride attire.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi506sa/o/research/digi506sa-(191).html
For a mom, watching your daughter stroll down the aisle and marry the love of her life is an unforgettable moment.
https://digi51sa.ams3.digitaloceanspaces.com/research/digi51sa-(237).html
Moms who wish to give a little drama, consider vivid hues and statement options.
https://digi599sa.z29.web.core.windows.net/research/digi599sa-(262).html
The beaded flowers down one side add a tactile contact of luxury to the column costume .
https://storage.googleapis.com/digi467sa/research/digi467sa-(263).html
For the mother who likes to look put collectively and trendy, a jumpsuit in slate grey is bound to wow.
https://storage.googleapis.com/digi473sa/research/digi473sa-(107).html
This off-the-shoulder fashion would look great with a pair of strappy stilettos and shoulder-duster earrings.
https://je-tall-marketing-789.tor1.digitaloceanspaces.com/research/je-marketing-(49).html
For her, that included a couture Karen Sabag ball gown match for a princess.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi502sa/o/research/digi502sa-(19).html
You’ve helped her discover her dream dress, now allow us to allow you to find yours…
https://digi605sa.z12.web.core.windows.net/research/digi605sa-(407).html
Stylish blue navy costume with floral sample lace and great silk lining, three-quarter sleeve.
https://digi659sa.netlify.app/research/digi659sa-(226)
A mother is a ray of shine in a daughter’s life, and so she deserves to get all glitzy and gleamy in a sequin MOB gown.
https://digi657sa.netlify.app/research/digi657sa-(287)
Don’t be concerned with having every thing match completely.
https://je-tall-marketing-765.blr1.digitaloceanspaces.com/research/je-marketing-(165).html
Much like the mother of the groom, step-mothers of both the bride or groom should observe the lead of the mother of the bride.
https://je-tall-marketing-770.blr1.digitaloceanspaces.com/research/je-marketing-(374).html
As the mother of the bride, your position comes with big responsibilities.
https://je-sf-tall-marketing-712.b-cdn.net/research/je-marketing-(364).html
Pair the dress with impartial or metallic equipment to keep the the rest of the look subtle and easy.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(500).html
From impartial off-white numbers to daring, punchy, and fashion-forward designs, there’s one thing right here that may swimsuit her fancy.
https://storage.googleapis.com/digi460sa/research/digi460sa-(308).html
Kay Unger’s maxi romper combines the look of a maxi costume with pants.
https://digi611sa.z28.web.core.windows.net/research/digi611sa-(349).html
Make it pop with a blinged-out pair of heels and matching equipment.
https://storage.googleapis.com/digi474sa/research/digi474sa-(198).html
Another can’t-miss palettes for mother of the bride or mother of the groom dresses?
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi510sa/o/research/digi510sa-(284).html
This mother’s knee-length patterned dress completely matched the temper of her kid’s outdoor wedding ceremony venue.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi511sa/o/research/digi511sa-(136).html
Floral prints and gentle colours play nicely with decor that’s sure to embrace the blooms of the spring and summer time months.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(207).html
There often aren’t any set rules in phrases of MOB outfits for the wedding.
https://je-tall-marketing-764.sgp1.digitaloceanspaces.com/research/je-marketing-(347).html
It’s usually common follow to avoid wearing white, ivory or cream.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi509sa/o/research/digi509sa-(490).html
For mothers who swoon for all things sassy, the dramatic gold mother of the bride costume could be the picture-perfect decide in 2022.
https://je-tall-marketing-821.syd1.digitaloceanspaces.com/research/je-marketing-(91).html
This glittery lace-knit two-piece includes a sleeveless cocktail gown and coordinating longline jacket.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(241).html
This mother of the bride outfit channels pure femininity.
https://je-tall-marketing-823.tor1.digitaloceanspaces.com/research/je-marketing-(500).html
At as soon as effortless and refined, this beautifully draped robe is the perfect hue for a fall marriage ceremony.
https://je-tall-marketing-803.lon1.digitaloceanspaces.com/research/je-marketing-(254).html
The finest mother of the bride dresses fill you with confidence on the day and are comfortable sufficient to wear all day and into the evening.
https://je-tall-marketing-795.lon1.digitaloceanspaces.com/research/je-marketing-(307).html
This desert colored gown is ideal if what the bride desires is so that you can put on a colour closer to white.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(474).html
An alternative is to combine black with one other colour, which may look very chic.
https://je-tall-marketing-787.lon1.digitaloceanspaces.com/research/je-marketing-(375).html
Jovani Plus measurement mother of the bride attire fits any body kind.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(496).html
The flowy silhouette and flutter sleeves hit the proper playful observe for spring and summer season celebrations.
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(493).html
Tadashi Shoji is a good name to look out for when you’re on the hunt for a designer gown.
https://storage.googleapis.com/digi477sa/research/digi477sa-(340).html
A fit-and-flare silhouette will accentuate your figure but still feel light and ethereal.
https://je-sf-tall-marketing-722.b-cdn.net/research/je-marketing-(253).html
If you like impartial tones, gold and silver clothes are promising selections for an MOB!
https://storage.googleapis.com/digi469sa/research/digi469sa-(39).html
Make certain you’re both carrying the identical formality of costume as properly.
https://je-tall-marketing-822.sgp1.digitaloceanspaces.com/research/je-marketing-(333).html
Plus, a blouson sleeve and a ruched neckline add to this silhouette’s romantic vibe.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi503sa/o/research/digi503sa-(127).html
Similar to the mothers of the bride and groom, the grandmothers might want to coordinate with the marriage party.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-1/research/je-marketing-(83).html
For her, that included a couture Karen Sabag ball gown fit for a princess.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-7/research/je-marketing-(217).html
This combination is especially great for summer time weddings.
https://je-tall-marketing-772.sgp1.digitaloceanspaces.com/research/je-marketing-(167).html
Discover one of the best wedding visitor outfits for women and men for all seasons.
https://digi660sa.netlify.app/research/digi660sa-(165)
Go for prints that talk to your marriage ceremony location, and most significantly, her private fashion.
https://je-tall-marketing-780.blr1.digitaloceanspaces.com/research/je-marketing-(399).html
From neutral off-white numbers to bold, punchy, and fashion-forward designs, there’s one thing here that can swimsuit her fancy.
https://storage.googleapis.com/digi462sa/research/digi462sa-(268).html
Take inspiration from the bridesmaid attire and communicate to your daughter to get some ideas on colors that will work nicely on the day.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(392).html
So long as you’ve got obtained the soonlyweds’ approval, there’s absolutely nothing incorrect with an allover sequin robe.
https://digi64sa.sfo3.digitaloceanspaces.com/research/digi64sa-(280).html
One reviewer mentioned they wore a white jacket excessive however you would additionally select a wrap or bolero.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi511sa/o/research/digi511sa-(105).html
We even have tea-length dresses and long dresses to go properly with any season, venue or preference.
https://je-tall-marketing-802.fra1.digitaloceanspaces.com/research/je-marketing-(3).html
Sort via our full choice of clothes to search out your good fit in many colours and any size.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(160).html
Colors corresponding to fuchsia, green and silver are just a few ideas!
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(422).html
Keep in mind that many web sites let you filter clothes by color, silhouette, length, and neckline.
https://je-tall-marketing-790.sgp1.digitaloceanspaces.com/research/je-marketing-(269).html
Jovani provides you the highest very finest quality MOB robes for a low price.
https://je-tall-marketing-804.tor1.digitaloceanspaces.com/research/je-marketing-(52).html
If you’re a Nordstrom regular, you may be pleased to know the beloved retailer has an extensive collection of mother-of-the-bride dresses.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-9/research/je-marketing-(375).html
Another dress with ruching for you as I suppose ruched styles are so flattering.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-6/research/je-maarketing-(278).html
Celebrate their massive day in fashion with our Mother of the Bride or Groom outfits.
https://storage.googleapis.com/digi477sa/research/digi477sa-(490).html
Discover one of the best wedding ceremony guest outfits for women and men for all seasons.
https://je-tall-marketing-804.tor1.digitaloceanspaces.com/research/je-marketing-(365).html
You can also coordinate with the MOB to verify your decisions complement one another.
https://digi654sa.netlify.app/research/digi654sa-(273)
This robe in timeless black is flocked with shimmering sequins and eyecatching beadwork.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(430).html
You can complement it in a selection of ways, from a simple no-makeup look to bold pink lipstick paired with smokey eyes and much more.
https://storage.googleapis.com/digi473sa/research/digi473sa-(476).html
Sleeveless, short-sleeved, or 3/4 size, there is an possibility for almost everyone!.
https://je-tall-marketing-786.tor1.digitaloceanspaces.com/research/je-marketing-(354).html
Make sure you have the perfect gown, sneakers, and extra to look excellent on the big day.
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(333).html
“I wished my women to have fun,” the bride stated of the selection.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(192).html
Encourage your mother to have a little fun when dressing for your ceremony or rehearsal dinner.
https://je-tall-marketing-815.lon1.digitaloceanspaces.com/research/je-marketing-(222).html
The costume is figure-hugging and provides a easy silhouette.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(489).html
Jovani is a trendy but straightforward brand that caters to the trendy girl.
https://storage.googleapis.com/digi470sa/research/digi470sa-(356).html
The costume is figure-hugging and presents a easy silhouette.
https://digi648sa.netlify.app/research/digi648sa-(249)
Look and feel truly elegant on this lengthy dress without stealing all the attention from the bride.
https://digi600sa.z45.web.core.windows.net/research/digi600sa-(202).html
Both the mother of the bride and the mom of the groom chose hanging gowns with embellishment and phantasm necklines for this outdoor celebration.
https://je-tall-marketing-775.tor1.digitaloceanspaces.com/research/je-marketing-(407).html
This also helps leave time for transport in case the costume takes longer than expected to arrive.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi511sa/o/research/digi511sa-(255).html
Find the proper affordable marriage ceremony visitor clothes for any season.
https://storage.googleapis.com/digi458sa/research/digi458sa-(156).html
Of course, you possibly can play with colors of sequin outfits to kick off the look of your desires.
https://digi56sa.sfo3.digitaloceanspaces.com/research/digi56sa-(277).html
Find the best tie types for 2021 and past for your wedding.
https://je-tall-marketing-774.lon1.digitaloceanspaces.com/research/je-marketing-(197).html
Choose a gown with structure that holds its form all by itself.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(101).html
Her strapless and blush pink gown, with textured floral particulars and an embellished belt, had this mother smiling from ear to ear.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(244).html
I really have 2 children who have actually the age of getting maried 30 and 34.
https://storage.googleapis.com/digi459sa/research/digi459sa-(320).html
Sophie Moore is a former Brides editor and present contributing writer.
https://je-tall-marketing-787.lon1.digitaloceanspaces.com/research/je-marketing-(102).html
Available in 14 colors, you’re positive to find a gown that matches your daughter or son’s wedding theme.
https://je-tall-marketing-797.fra1.digitaloceanspaces.com/research/je-marketing-(239).html
Look for dresses in champagne, navy and even black (yes, it is totally fashionable to put on black to a wedding!) for a refined color palette.
https://digi650sa.netlify.app/research/digi650sa-(60)
Current in style trends function lace, prints, fashionable empire waistlines and jackets.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(106).html
Some ladies choose to put on a gown, while others choose separates…and both are great options!
https://storage.googleapis.com/digi475sa/research/digi475sa-(117).html
The monochrome design creates a streamlined look, while crystals, beads and sequins add just the appropriate amount of razzle-dazzle.
https://storage.googleapis.com/digi461sa/research/digi461sa-(291).html
Many of the choices above would help you to hide slightly little bit of a tummy.
https://digi599sa.z29.web.core.windows.net/research/digi599sa-(149).html
A purple lace Erdem gown, embroidered with pink and crimson blooms, paired perfectly with this trendy mom’s half-up, half-down coiffure.
https://digi64sa.sfo3.digitaloceanspaces.com/research/digi64sa-(241).html
So, at the very least, both mothers will want to wear colors that complement the other.
https://je-tall-marketing-780.blr1.digitaloceanspaces.com/research/je-marketing-(116).html
If you are a Nordstrom regular, you’ll be happy to know the beloved retailer has an in depth assortment of mother-of-the-bride clothes.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi500sa/o/research/digi500sa-(438).html
It is customary to keep away from wearing white on your children’s wedding ceremony day.
https://je-tall-marketing-790.sgp1.digitaloceanspaces.com/research/je-marketing-(265).html
Ahead, 25 mother-of-the-bride seems that feel fashion-forward, elegant, and of-the-moment for a return to weddings later this yr and into 2022.
https://storage.googleapis.com/digi465sa/research/digi465sa-(127).html
When shopping for mother of the bride clothes, firstly, think about the overall dress code on the invite.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi511sa/o/research/digi511sa-(162).html
Keep issues basic or strive variations of the shades, like a champagne, rose gold, or shimmery charcoal.
https://storage.googleapis.com/digi474sa/research/digi474sa-(296).html
Don’t be afraid to make an announcement in head-to-toe sparkle.
https://digi651sa.netlify.app/research/digi651sa-(212)
Inspired by bold flowers, a blooming print pops off every inch of this strapless ball robe, from the illusion plunge corset bodice to the total, sweeping skirt.
https://je-tall-marketing-808.sgp1.digitaloceanspaces.com/research/je-marketing-(273).html
David’s Bridal presents convenient online and in-person purchasing experiences.
https://je-tall-marketing-792.blr1.digitaloceanspaces.com/research/je-marketing-(24).html
But, if I may add some private advice, ENJOY the journey and strategy of it.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(204).html
Speak to your daughter about the feel of the marriage day; is it a black tie affair?
https://digi649sa.netlify.app/research/digi649sa-(370)
The cowl neck adds some very refined sex appeal, the ruching helps to cover any lumps and bumps and the 3D flowers add a sense of luxurious.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(157).html
Knowing somewhat bit about what you’d like to wear may help you slim down your selections.
https://je-tall-marketing-801.sgp1.digitaloceanspaces.com/research/je-marketing-(28).html
The dress has flattering free chiffon sleeves, a relaxed tie waist, and intricate beading work.
https://storage.googleapis.com/digi473sa/research/digi473sa-(210).html
So, in case your kids are internet hosting a black tie affair, make certain to put on a floor-length gown—preferably in a impartial tone .
https://je-tall-marketing-795.lon1.digitaloceanspaces.com/research/je-marketing-(323).html
This bride’s mom donned a stunning sari for her daughter’s marriage ceremony.
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(340).html
Her strapless and blush pink robe, with textured floral particulars and an embellished belt, had this mother smiling from ear to ear.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(159).html
The distinction between these two gowns is in how they are chosen.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(300).html
Sheer stretch tulle and cap sleeves on the neckline add an eye-catching detail, giving the illusion of a strapless look.
https://digi606sa.z48.web.core.windows.net/research/digi606sa-(483).html
Shop gorgeous wedding ceremony attire for the mother-of-the-bride in standard, plus and petite sizes at Adrianna Papell.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(232).html
It is also recommended to keep away from black clothes as these often symbolize times of mourning.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi507sa/o/research/digi507sa-(144).html
The bridesmaids at this at-home Kentucky marriage ceremony sparkled in gold-sequined mini dresses.
https://digi647sa.netlify.app/research/digi647sa-(96)
Speak with the bride to get her thoughts on this and see what’s available in retailers and online.
https://storage.googleapis.com/digi462sa/research/digi462sa-(88).html
Avoid flashy shades like shiny red, pink or yellow because the gown might stand out an excessive amount of.
https://je-tall-marketing-809.lon1.digitaloceanspaces.com/research/je-marketing-(306).html
But it’s important to check in with the bride before you make any selections.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi505sa/o/research/digi505sa-(204).html
Otherwise, photographs will seem off-balanced, and it may be misconstrued that one mom is attempting to outshine or outdo the opposite.
https://je-tall-marketing-812.fra1.digitaloceanspaces.com/research/je-marketing-(22).html
Use the filters to kind by silhouette, neckline, fabric, and length.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-7/research/je-marketing-(94).html
Embellished with beautiful ornate beading, this gown will catch the light from each angle.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi502sa/o/research/digi502sa-(197).html
You may, of course, select a maxi gown on your special occasion.
https://digi63sa.sfo3.digitaloceanspaces.com/research/digi63sa-(226).html
With cap sleeves and an phantasm neckline, this fitted blue magnificence was excellent for this D.C.
https://je-tall-marketing-808.sgp1.digitaloceanspaces.com/research/je-marketing-(66).html
Pair the gown with impartial or metallic accessories to keep the relaxation of the look refined and simple.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi507sa/o/research/digi507sa-(423).html
You’ll merely glow on this shimmering gold gown by Aidan Mattox.
https://digi72sa.sfo3.digitaloceanspaces.com/research/digi71sa-(147).html
As a mother of a daughter who is already married, the looking for both her costume and mine was one of many highlights of the wedding planning.
https://storage.googleapis.com/digi460sa/research/digi460sa-(349).html
Another necessary tip for dressing in your daughter’s big day is to let her bridal fashion guide you.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-1/research/je-marketing-(430).html
The straps and sleeves you choose on your gown will affect the neckline and shape of your costume.
https://storage.googleapis.com/digi462sa/research/digi462sa-(302).html
You can discover a great choice right here and they are great high quality that won’t break the bank.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-6/research/je-marketing-(126).html
The mother of the bride’s Oscar de la Renta gown was such a hit, it really inspired the bridesmaids’ bouquets.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi506sa/o/research/digi506sa-(352).html
Clean strains and a formed waist make this a timeless and chic mom of the bride costume with a flattering silhouette.
https://je-tall-marketing-781.fra1.digitaloceanspaces.com/research/je-marketing-(276).html
I was very impressed to see that there are classy and elegant outfits for all plus dimension girls.
https://digi60sa.fra1.digitaloceanspaces.com/research/digi60sa-(240).html
But the most important piece of apparel you will choose main as much as your kid’s wedding?
https://digi648sa.netlify.app/research/digi648sa-(169)
Whether you could have your heart on embroidery, embellishment, sequin, or ruched silk smoothness, golden clothes look great in all styles and designs.
https://storage.googleapis.com/digi476sa/research/digi476sa-(456).html
Guests love to watch the joy and satisfaction appear on your face as you watch your daughter marry their greatest good friend.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(173).html
We’ve at all times heard that mom is aware of best, and if these moms of the bride—and mothers of the groom!
https://storage.googleapis.com/digi462sa/research/digi462sa-(370).html
From inexpensive and trendy to designer and conventional, these are our favorite bow ties for weddings.
https://je-tall-marketing-781.fra1.digitaloceanspaces.com/research/je-marketing-(364).html
Remember, you will have a look at these photographs in years to come back.
https://storage.googleapis.com/digi461sa/research/digi461sa-(227).html
Beach weddings are more laid-back and informal than different forms of nuptials—and a proper gown would really feel out of place.
https://storage.googleapis.com/digi477sa/research/digi477sa-(156).html
Discover trendy jumpsuits and clothes with complementing jackets, fascinators, shoes and accessories to complete your look.
https://digi51sa.ams3.digitaloceanspaces.com/research/digi51sa-(339).html
As mother of the bride, you could wish to discover a look which enhances these parts, without being matchy-matchy.
https://digi55sa.nyc3.digitaloceanspaces.com/research/digi55sa-(86).html
MOB etiquettes say if black flatters you, all–black could be your go-to mom of the bride or mother of the groom on the lookout for the big day.
https://digi597sa.z1.web.core.windows.net/research/digi597sa-(271).html
For a seaside marriage ceremony I would put on something a bit extra flowy like the flowery and ruffly dresses above.
https://je-tall-marketing-767.sgp1.digitaloceanspaces.com/research/je-marketing-(485).html
This MOB costume falls slightly below the knee, so take the chance to indicate off a killer pair of heels.
https://digi647sa.netlify.app/research/digi647sa-(259)
This dress, as its name suggests, is extremely elegant.
https://digi48sa.sfo3.digitaloceanspaces.com/research/digi48sa-(258).html
This gown in timeless black is flocked with shimmering sequins and eyecatching beadwork.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(152).html
Reviewers describe it as very slimming and say the beadwork is beautiful.
https://digi56sa.sfo3.digitaloceanspaces.com/research/digi56sa-(84).html
One reviewer mentioned they wore a white jacket excessive but you can also choose a wrap or bolero.
https://digi608sa.z44.web.core.windows.net/research/digi608sa-(352).html
You may, in fact, select a maxi gown for your special day.
https://storage.googleapis.com/digi466sa/research/digi466sa-(441).html
Read on for the most effective mom of the bride dresses for each season, body kind, and price range.
https://digi656sa.netlify.app/research/digi656sa-(137)
Before you start your search (around the six- to eight-month mark), brush up on mother-of-the-bride apparel etiquette.
https://digi597sa.z1.web.core.windows.net/research/digi597sa-(388).html
If you’re in a pinch, many e-commerce sites like Net-a-Porter or Nordstrom provide rush shipping.
https://storage.googleapis.com/digi458sa/research/digi458sa-(114).html
I might play a task in my stepdaughter’s wedding ceremony or I may not.
https://digi653sa.netlify.app/research/digi653sa-(236)
Wear yours with a strappy block heel–a stylish and sensible answer for an outside marriage ceremony.
https://je-tall-marketing-782.fra1.digitaloceanspaces.com/research/je-marketing-(384).html
Thus, it is important to talk to the bride to ask about what the wedding will be like.
https://digi64sa.sfo3.digitaloceanspaces.com/research/digi64sa-(471).html
Look for clothes in champagne, navy and even black (yes, it’s completely fashionable to wear black to a wedding!) for a refined color palette.
https://je-tall-marketing-783.blr1.digitaloceanspaces.com/research/je-marketing-(82).html
Neither a daytime occasion nor a proper summer season night soiree requires a full-length robe.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(28).html
Browse our prime alternatives and buy your favorite proper on the spot.
https://storage.googleapis.com/digi471sa/research/digi471sa-(165).html
One mom’s blush attire appeared stunning in opposition to these two brides’ romantic wedding ceremony clothes.
https://digi74sa.sfo3.digitaloceanspaces.com/research/digi74sa-(34).html
My daughter goals of a marriage on a seaside in Bali, so the place will that depart me I surprise.
https://digi602sa.z45.web.core.windows.net/research/digi602sa-(230).html
This retro and chic cocktail dress contains a full-lace overlay good for a night marriage ceremony.
https://digi659sa.netlify.app/research/digi659sa-(323)
Montage by Mon Cheri designer Ivonne Dome designs this big day line with the subtle, fashion-forward mom in mind.
https://digi649sa.netlify.app/research/digi649sa-(30)
Opt for non-creasing, moveable fabrics similar to scuba or lace, teamed with trendy but practical sneakers for that added touch of glamour.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi506sa/o/research/digi506sa-(148).html
The mother of the bride and mom of the groom often wear fully different dress styles and colors.
https://digi651sa.netlify.app/research/digi651sa-(29)
Pink anemones and blue and yellow wildflower buds accented this beautiful black dress worn by the mom of the bride.
https://storage.googleapis.com/digi461sa/research/digi461sa-(199).html
You might go for a traditional shade similar to navy, or select a summery color like the Eliza j ruched waist jumpsuit .
https://storage.googleapis.com/digi471sa/research/digi471sa-(364).html
This glittery lace-knit two-piece includes a sleeveless cocktail dress and coordinating longline jacket.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(353).html
Plus, a blouson sleeve and a ruched neckline add to this silhouette’s romantic vibe.
https://je-tall-marketing-771.lon1.digitaloceanspaces.com/research/je-marketing-(22).html
Whether you may have your heart on embroidery, embellishment, sequin, or ruched silk smoothness, golden attire look nice in all kinds and designs.
https://je-tall-marketing-808.sgp1.digitaloceanspaces.com/research/je-marketing-(132).html
From reasonably priced and classy to designer and traditional, these are our favorite bow ties for weddings.
https://digi63sa.sfo3.digitaloceanspaces.com/research/digi63sa-(29).html
That mentioned, having such a broad variety of options might really feel somewhat overwhelming.
https://je-tall-marketing-793.tor1.digitaloceanspaces.com/research/je-marketing-(219).html
A navy cut-out overlay added a cool geometric pattern to a blush pink skirt.
https://je-tall-marketing-776.blr1.digitaloceanspaces.com/research/je-marketing-(67).html
Think about jewelry, shoes and handbags – all issues that can assist make your mom of the bride outfit distinctive.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(263).html
To make hers, mom JoJo Cohen turned to her shut pal, the late designer L’Wren Scott.
https://digi57sa.sfo3.digitaloceanspaces.com/research/digi57sa-(426).html
This will help her discover the complementary ensemble and forestall her from being over or underdressed.
https://je-sf-tall-marketing-722.b-cdn.net/research/je-marketing-(73).html
This funky floral print mother-of-the-bride costume offers us all of the ’70s vibes .
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(227).html
Let the answers to some of our most regularly asked questions guide you in the right direction.
https://je-tall-marketing-764.sgp1.digitaloceanspaces.com/research/je-marketing-(479).html
You’ve helped her find her dream dress, now let us assist you to discover yours…
https://je-tall-marketing-767.sgp1.digitaloceanspaces.com/research/je-marketing-(387).html
Wear yours with heels in a impartial tone and delicate shoulder-grazing earrings.
https://storage.googleapis.com/digi472sa/research/digi472sa-(79).html
Follow the styling lead and pair yours with silver sandals and a berry lip.
https://storage.googleapis.com/digi474sa/research/digi474sa-(320).html
One mom’s blush attire appeared lovely in opposition to these two brides’ romantic marriage ceremony clothes.
https://digi67sa.sfo3.digitaloceanspaces.com/research/digi66sa-(263).html
Speak to your daughter about the really feel of the wedding day; is it a black tie affair?
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(177).html
Make a beautiful impression on this floral printed ball robe that includes wrap-around ties that spotlight your waist and helpful hidden pockets.
https://digi608sa.z44.web.core.windows.net/research/digi608sa-(56).html
Pink anemones and blue and yellow wildflower buds accented this pretty black costume worn by the mother of the bride.
https://je-tall-marketing-778.fra1.digitaloceanspaces.com/research/je-marketing-(41).html
Moms who need to give somewhat drama, consider vivid hues and statement options.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(226).html
With choices in any neckline or silhouette, appear to be A line, strapless, Taffeta, organza, and lace.
https://storage.googleapis.com/digi465sa/research/digi465sa-(343).html
Her mom, who similarly sparkled in a gold silk dupioni floor-length skirt go nicely with.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(211).html
The high-end retailer sells plenty of coveted luxury brands like Monique Lhuillier, THEIA, Jenny Packham, Badgley Mischka and more.
https://storage.googleapis.com/digi468sa/research/digi468sa-(259).html
Read on for one of the best mom of the bride attire for every season, physique sort, and budget.
https://storage.googleapis.com/digi473sa/research/digi473sa-(134).html
Available in 14 colours, you may be sure to find a robe that matches your daughter or son’s wedding theme.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(258).html
To allow you to in your search, we’ve done the onerous work for you!
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(499).html
Spring mom of the bride clothes are going to depend on how sizzling or cold your springs are.
https://digi604sa.z31.web.core.windows.net/research/digi604sa-(386).html
Both the mom of the bride and the mother of the groom selected striking robes with embellishment and illusion necklines for this outside celebration.
https://digi74sa.sfo3.digitaloceanspaces.com/research/digi74sa-(278).html
From neutral off-white numbers to bold, punchy, and fashion-forward designs, there’s one thing right here that can swimsuit her fancy.
https://je-tall-marketing-791.sgp1.digitaloceanspaces.com/research/je-marketing-(274).html
The costume has flattering unfastened chiffon sleeves, a relaxed tie waist, and complicated beading work.
https://storage.googleapis.com/digi476sa/research/digi476sa-(314).html
Otherwise, photos will seem off-balanced, and it may be misconstrued that one mother is attempting to outshine or outdo the other.
https://digi61sa.nyc3.digitaloceanspaces.com/research/digi61sa-(269).html
For a seashore wedding ceremony I would wear something a bit extra flowy just like the flowery and ruffly clothes above.
https://storage.googleapis.com/digi458sa/research/digi458sa-(235).html
Spring and summer time weddings name for gentle tones, floral motifs, and a romantic flair.
https://digi597sa.z1.web.core.windows.net/research/digi597sa-(362).html
Her mom, who similarly sparkled in a gold silk dupioni floor-length skirt go properly with.
https://je-tall-marketing-792.blr1.digitaloceanspaces.com/research/je-marketing-(261).html
Another important tip for dressing in your daughter’s massive day is to let her bridal style information you.
https://digi54sa.syd1.digitaloceanspaces.com/research/digi54sa-(287).html
This mother of the bride escorted her daughter down the aisle in a light-weight blue gorgeous halter gown.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(469).html
But, if I could add some personal advice, ENJOY the journey and process of it.
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(180).html
Always costume for comfort and to please what the bride has in mind.
https://digi648sa.netlify.app/research/digi648sa-(332)
Think oh-so-elegant bags and fascinators that’ll complete your Mother of the Bride outfit in serious type.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(476).html
Another necessary tip for dressing on your daughter’s huge day is to let her bridal type information you.
https://storage.googleapis.com/digi470sa/research/digi470sa-(38).html
With cap sleeves and an phantasm neckline, this fitted blue magnificence was perfect for this D.C.
https://digi63sa.sfo3.digitaloceanspaces.com/research/digi63sa-(361).html
The bridesmaids collected the recipes and created them right into a newlyweds cookery guide that they gave the couple up their day.
https://digi48sa.sfo3.digitaloceanspaces.com/research/digi48sa-(297).html
One of the proudest and most anticipated days in a mother’s life is the day that her daughter or son gets married.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(156).html
Whatever the situation, when you are ready to attend a marriage, you’ll wish to look your finest.
https://digi658sa.netlify.app/research/digi658sa-(378)
Shimmering metallic tones are good for a fall or winter wedding.
https://je-tall-marketing-778.fra1.digitaloceanspaces.com/research/je-marketing-(491).html
Then, let the formality, season and venue of the marriage be your guide.
https://je-tall-marketing-773.blr1.digitaloceanspaces.com/research/je-marketing-(483).html
Don’t be afraid of anything oversized—the large bow of this robe will flatter small busts, and make waists and arms appear petite as compared.
https://je-tall-marketing-795.lon1.digitaloceanspaces.com/research/je-marketing-(143).html
Her mother, who similarly sparkled in a gold silk dupioni floor-length skirt suit.
https://digi651sa.netlify.app/research/digi651sa-(107)
This glittery lace-knit two-piece features a sleeveless cocktail costume and coordinating longline jacket.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(341).html
Don’t be involved with having every thing match completely.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-6/research/je-marketing-(146).html
Talk to your daughter or future daughter- in-law to get a really feel for the visual she’s attempting to create.
https://storage.googleapis.com/digi463sa/research/digi463sa-(390).html
A stylishly easy occasion gown printed with romantic florals, excellent for the mother of the bride.
https://je-sf-tall-marketing-722.b-cdn.net/research/je-marketing-(428).html
Jewel tones are an ideal palette for mothers of the bride and grooms year-round.
https://je-tall-marketing-823.tor1.digitaloceanspaces.com/research/je-marketing-(120).html
So lengthy as you have received the soonlyweds’ approval, there’s completely nothing mistaken with an allover sequin robe.
https://je-tall-marketing-778.fra1.digitaloceanspaces.com/research/je-marketing-(89).html
You will wish to wear lighter colours, or whatever your daughter suggests.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(382).html
Don’t be involved with having every thing match perfectly.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(437).html
Check out our choices for petite mom of the bride dresses!
https://digi606sa.z48.web.core.windows.net/research/digi606sa-(437).html
The straight hemline on the bottom falls simply above the ankles and the sleeves stop right after the elbows.
https://storage.googleapis.com/digi465sa/research/digi465sa-(206).html
This gown’ dreamy chiffon cape feels ceremonial and refined, and is easily removed to reveal a slinkier metallic sheath beneath for dinner and dancing.
https://storage.googleapis.com/digi462sa/research/digi462sa-(149).html
However, coordination is still essential for chic images on the big day.
https://je-tall-marketing-817.ams3.digitaloceanspaces.com/research/je-marketing-(57).html
Make positive you may have the proper costume, sneakers, and extra to look excellent on the large day.
https://digi78sa.sfo3.digitaloceanspaces.com/research/digi78sa-(266).html
Encourage your mom to have slightly enjoyable when dressing on your ceremony or rehearsal dinner.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-2/research/je-marketing-(21).html
Make positive you’re each wearing the identical formality of dress as well.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(303).html
Our mothers are attractive and amazing and they want to rock what they’ve.
https://digi58sa.ams3.digitaloceanspaces.com/research/digi58sa-(332).html
No, you shouldn’t match with bridesmaids; instead, complement them.
https://digi601sa.z45.web.core.windows.net/research/digi601sa-(144).html
And lastly, don’t worry about trying to solely ‘age-appropriate’ boutiques.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi510sa/o/research/digi510sa-(494).html
Black is just about accepted these days, no matter the event.
https://storage.googleapis.com/digi463sa/research/digi463sa-(221).html
If you like your legs, you might want to go with an above-the-knee or just-below-the-knee gown.
https://digi652sa.netlify.app/research/digi652sa-(421)
However, to determine whether or not you must also coordinate with both moms, examine in with the bride.
https://je-sf-tall-marketing-726.b-cdn.net/research/je-marketing-(124).html
This beautiful gown is produced from double-stretch Mikado for a streamlined, snug fit.
https://digi660sa.netlify.app/research/digi660sa-(53)
For the redwood location, it will be great to wear one thing in natural colours like the 2 moss green outfits pictured.
https://je-tall-marketing-792.blr1.digitaloceanspaces.com/research/je-marketing-(98).html
The clothes on this class characteristic attire with parts corresponding to exquisite embroidery and floral accents.
https://je-tall-marketing-818.fra1.digitaloceanspaces.com/research/je-marketing-(234).html
In short, sure, however provided that it goes with the feel of the day.
https://digi54sa.syd1.digitaloceanspaces.com/research/digi54sa-(476).html
A twinset can have a “fuddy duddy” popularity, but it positively doesn’t have to look old fashioned.
https://storage.googleapis.com/digi462sa/research/digi462sa-(216).html
This surprisingly inexpensive mother-of-the-bride dress is perfect for a formal fall or winter wedding ceremony.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi509sa/o/research/digi509sa-(229).html
Looking at summer time mom of the bride clothes which would possibly be a step away from the norm?
https://je-tall-marketing-791.sgp1.digitaloceanspaces.com/research/je-marketing-(14).html
Think about jewelry, sneakers and purses – all things that may assist make your mother of the bride outfit unique.
https://digi651sa.netlify.app/research/digi651sa-(465)
Experiment with strapless types, unexpected lengths, or modern jumpsuits.
https://je-tall-marketing-774.lon1.digitaloceanspaces.com/research/je-marketing-(324).html
We even have tea-length clothes and long dresses to swimsuit any season, venue or preference.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(270).html
Wear yours with heels in a neutral tone and delicate shoulder-grazing earrings.
https://storage.googleapis.com/digi460sa/research/digi460sa-(30).html
You can buy lengthy sleeves, a protracted lace mom of the bride dress, or a lovely ballgown with a boat neckline.
https://je-sf-tall-marketing-714.b-cdn.net/research/je-marketing-(282).html
In addition, many kinds are available with matching jackets or shawls for ultimate versatility.
https://je-tall-marketing-798.blr1.digitaloceanspaces.com/research/je-marketing-(22).html
However, the only rule for wearing sequin clothes is to maintain equipment and makeup subtle.
https://je-tall-marketing-769.blr1.digitaloceanspaces.com/research/je-marketing-(302).html
Are you on the lookout for mother of the bride robes for summer time beach wedding?
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi506sa/o/research/digi506sa-(178).html
It has over one hundred forty positive evaluations, many from girls who wore this to a wedding and beloved it!
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-8/research/je-marketing-(156).html
This outfit’s intricate corded embroidery and understated black skirt are a match made in heaven—just like your daughter and their soon-to-be spouse.
https://digi54sa.syd1.digitaloceanspaces.com/research/digi54sa-(220).html
I can guarantee you that I won’t ever make that mistake again.
https://digi72sa.sfo3.digitaloceanspaces.com/research/digi71sa-(24).html
Florals set on black or dark backgrounds feel no less romantic but certainly deliver the delightfully surprising.
https://je-tall-marketing-790.sgp1.digitaloceanspaces.com/research/je-marketing-(276).html
Similar to the mothers of the bride and groom, the grandmothers may wish to coordinate with the marriage celebration.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(364).html
She’s a superhero to you and your entire household, so why not let her costume the part.
https://je-tall-marketing-808.sgp1.digitaloceanspaces.com/research/je-marketing-(91).html
Reviewers describe it as very slimming and say the beadwork is exquisite.
https://je-tall-marketing-783.blr1.digitaloceanspaces.com/research/je-marketing-(60).html
This brocade robe draws the eye to all the right places—from a touch of pores and skin on the shoulder to a ruched waist.
https://storage.googleapis.com/digi464sa/research/digi464sa-(315).html
This brocade robe draws the eye to all the best places—from a touch of pores and skin on the shoulder to a ruched waist.
https://digi649sa.netlify.app/research/digi649sa-(337)
You do not need to wait until last minute to get your gown on your child’s marriage ceremony.
https://digi647sa.netlify.app/research/digi647sa-(53)
As a mother of a daughter who’s already married, the shopping for each her gown and mine was one of the highlights of the wedding planning.
https://storage.googleapis.com/digi463sa/research/digi463sa-(181).html
The bridesmaids collected the recipes and created them into a newlyweds cookery book that they gave the couple up their day.
https://storage.googleapis.com/digi476sa/research/digi476sa-(350).html
Find the perfect inexpensive marriage ceremony visitor dresses for any season.
https://digi657sa.netlify.app/research/digi657sa-(261)
It’s often widespread apply to keep away from carrying white, ivory or cream.
https://je-tall-marketing-810.fra1.digitaloceanspaces.com/research/je-marketing-(357).html
Much like the mom of the groom, step-mothers of both the bride or groom ought to comply with the lead of the mother of the bride.
https://digi611sa.z28.web.core.windows.net/research/digi611sa-(288).html
Discover the most effective wedding ceremony visitor outfits for men and women for all seasons.
https://storage.googleapis.com/digi469sa/research/digi469sa-(91).html
Plus, the silhouette of this robe will look that instead more show-stopping as the cape wafts down the aisle to disclose her silhouette as she moves.
https://je-tall-marketing-797.fra1.digitaloceanspaces.com/research/je-marketing-(391).html
Avoid flashy shades like shiny purple, pink or yellow as the dress may stand out an extreme quantity of.
https://digi657sa.netlify.app/research/digi657sa-(451)
She’s a superhero to you and your whole family, so why not let her dress the half.
https://je-tall-marketing-797.fra1.digitaloceanspaces.com/research/je-marketing-(267).html
The monochrome design creates a streamlined look, while crystals, beads and sequins add simply the right quantity of razzle-dazzle.
https://je-tall-marketing-816.blr1.digitaloceanspaces.com/research/je-marketing-(435).html
A stylishly simple occasion gown printed with romantic florals, excellent for the mom of the bride.
https://storage.googleapis.com/digi472sa/research/digi472sa-(230).html
You need her to feel snug on the massive day—especially when it is time for wedding photos.
https://digi605sa.z12.web.core.windows.net/research/digi605sa-(4).html
The beaded flowers down one side add a tactile touch of luxury to the column gown .
https://je-tall-marketing-793.tor1.digitaloceanspaces.com/research/je-marketing-(75).html
An various is to combine black with another colour, which might look very stylish.
https://je-tall-marketing-813.syd1.digitaloceanspaces.com/research/je-marketing-(370).html
You don’t need to wear shiny pink for example, if the style of the day is more organic and muted.
https://digi657sa.netlify.app/research/digi657sa-(301)
There is no set do’s and don’ts when it comes to color, solely to keep away from white.
https://storage.googleapis.com/digi467sa/research/digi467sa-(354).html
Whatever the scenario, when you are in a position to attend a wedding, you’ll want to look your best.
https://digi67sa.sfo3.digitaloceanspaces.com/research/digi66sa-(497).html
Looking for the best inspiration in your mother of the bride look?
https://je-tall-marketing-798.blr1.digitaloceanspaces.com/research/je-marketing-(93).html
As the mother of the bride, eyes might be on you almost as a lot as they are going to be on the happy couple.
https://je-tall-marketing-772.sgp1.digitaloceanspaces.com/research/je-marketing-(343).html
No, you shouldn’t match with bridesmaids; as an alternative, complement them.
https://digi605sa.z12.web.core.windows.net/research/digi605sa-(245).html
Keep the strains of communication open all through the wedding planning process.
https://storage.googleapis.com/digi469sa/research/digi469sa-(348).html
One of our favourite things about Karen Kane is that they are measurement inclusive and have choices for all sizes.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(384).html
Adhere to the dress code, and look to bridesmaids or the marriage robe for steering on daring patterns or embellishments.
https://digi58sa.ams3.digitaloceanspaces.com/research/digi58sa-(217).html
For the mom who likes to look put collectively and trendy, a jumpsuit in slate gray is bound to wow.
https://storage.googleapis.com/digi460sa/research/digi460sa-(409).html
As mother of the bride, you might need to discover a look which complements these components, with out being matchy-matchy.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-6/research/je-maarketing-(179).html
This contains most variations of white, corresponding to ivory and champagne.
https://storage.googleapis.com/digi477sa/research/digi477sa-(394).html
In common, you’ll do your finest to avoid matching with the bridesmaids or the moms of the couple getting married.
https://storage.googleapis.com/digi464sa/research/digi464sa-(261).html
One reviewer mentioned they wore a white jacket over the top however you could additionally choose a wrap or bolero.
https://digi47sa.nyc3.digitaloceanspaces.com/research/digi47sa-(136).html
Its expansive variety, changing into match and trendy design deem Montage the leader in Mother of the Bride and Mother of the Groom costume collections.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(37).html
Encourage your mother to have somewhat enjoyable when dressing for your ceremony or rehearsal dinner.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(221).html
Wear yours with a strappy block heel–a fashionable and sensible resolution for an out of doors wedding ceremony.
https://digi601sa.z45.web.core.windows.net/research/digi601sa-(470).html
Current well-liked trends feature lace, prints, trendy empire waistlines and jackets.
https://je-tall-marketing-782.fra1.digitaloceanspaces.com/research/je-marketing-(446).html
This mom wore a traditional hanbokwith floral and geometric embroidery to her daughter’s California ranch wedding ceremony.
https://je-tall-marketing-773.blr1.digitaloceanspaces.com/research/je-marketing-(108).html
The flowy silhouette and flutter sleeves hit the perfect playful note for spring and summer season celebrations.
https://digi610sa.z9.web.core.windows.net/research/digi610sa-(112).html
MOB etiquettes say if black flatters you, all–black could be your go-to mother of the bride or mom of the groom looking for the special day.
https://storage.googleapis.com/digi469sa/research/digi469sa-(448).html
No, you shouldn’t match with bridesmaids; as an alternative, complement them.
https://je-tall-marketing-793.tor1.digitaloceanspaces.com/research/je-marketing-(234).html
This sheath gown and sequin capelet mixture boasts a modest neckline and high-slit skirt making it without delay sophisticated and sexy.
https://storage.googleapis.com/digi473sa/research/digi473sa-(385).html
However, the graphic styling of the flowers offers the costume a modern look.
https://storage.googleapis.com/digi471sa/research/digi471sa-(482).html
Look for supplies like breezy chiffon, breathable mesh, or draping georgette for the last word seashore wedding attire.
https://je-tall-marketing-807.blr1.digitaloceanspaces.com/research/je-marketing-(170).html
Steer away from something too near white similar to champagne and beige colors without talking to your daughter beforehand.
https://je-sf-tall-marketing-717.b-cdn.net/research/je-marketing-(58).html
For this romantic marriage ceremony at Brooklyn’s Wythe Hotel, the bride’s mom selected a short-sleeved, full-length teal dress.
https://digi78sa.sfo3.digitaloceanspaces.com/research/digi78sa-(100).html
Shopping for a mom of the bride outfit is thrilling but it can be overwhelming at the similar time.
https://je-tall-marketing-768.lon1.digitaloceanspaces.com/research/je-marketing-(51).html
Embroidery is a timeless pattern, and it’s by no means hoped to exit of favor.
https://je-tall-marketing-782.fra1.digitaloceanspaces.com/research/je-marketing-(351).html
You can all the time add a wrap should you don’t need to show off your arms.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(494).html
Take inspiration from the bridesmaid attire and converse to your daughter to get some concepts on colors that may work well on the day.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(439).html
Mothers of Bride and Groom often have a type of ‘uniform’.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-7/research/je-marketing-(360).html
I really have personally made the mistake of sticking to a low budget for a high-profile event and I nonetheless remorse it today!
https://je-tall-marketing-797.fra1.digitaloceanspaces.com/research/je-marketing-(431).html
Try to find a lengthy gown, and most significantly snug.
https://je-tall-marketing-765.blr1.digitaloceanspaces.com/research/je-marketing-(389).html
You can easily reduce a dash by marrying your elegant mom of the bride gown in lace fabric with pearl jewellery and statement heels.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(202).html
Montage by Mon Cheri designer Ivonne Dome designs this special occasion line with the delicate, fashion-forward mother in thoughts.
https://storage.googleapis.com/digi458sa/research/digi458sa-(6).html
And lastly, don’t fear about seeking to only ‘age-appropriate’ boutiques.
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(335).html
Think oh-so-elegant baggage and fascinators that’ll full your Mother of the Bride outfit in critical style.
https://storage.googleapis.com/digi469sa/research/digi469sa-(199).html
Don’t be afraid to make a press release in head-to-toe sparkle.
https://digi656sa.netlify.app/research/digi656sa-(399)
You can nonetheless embrace these celebratory metallic shades without covering yourself head to toe in sequins.
https://digi650sa.netlify.app/research/digi650sa-(159)
Following these easy pointers are certain to make the process go smoothly and effectively.
https://digi67sa.sfo3.digitaloceanspaces.com/research/digi66sa-(63).html
Looking for the best inspiration for your mom of the bride look?
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(256).html
The mom of the bride and mother of the groom normally put on utterly different costume kinds and colours.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi498sa/o/research/digi498sa-(8).html
For a mom, watching your daughter stroll down the aisle and marry the love of her life is an unforgettable second.
https://je-tall-marketing-798.blr1.digitaloceanspaces.com/research/je-marketing-(488).html
Her strapless and blush pink robe, with textured floral details and an embellished belt, had this mom smiling from ear to ear.
https://storage.googleapis.com/digi464sa/research/digi464sa-(424).html
This candy and elegant midi with a built-in cape would look simply as stylish paired with an evening shoe as it will with a floor-length maxi.
https://je-tall-marketing-786.tor1.digitaloceanspaces.com/research/je-marketing-(44).html
One of the proudest and most anticipated days in a mother’s life is the day that her daughter or son gets married.
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(382).html
Its bateau neckline, three-quarter length sleeves, and full A-line skirt make it flattering, as well.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(271).html
For the redwood location, it might be nice to wear one thing in natural colors like the 2 moss green outfits pictured.
https://storage.googleapis.com/digi476sa/research/digi476sa-(438).html
Jules & Cleo, solely at David’s Bridal Polyester, nylon Back zipper; absolutely lined …
https://je-sf-tall-marketing-715.b-cdn.net/research/je-marketing-(28).html
The bridesmaids at this at-home Kentucky wedding ceremony sparkled in gold-sequined mini attire.
https://digi47sa.nyc3.digitaloceanspaces.com/research/digi47sa-(485).html
So, we’ve compiled a information to one of the best mother of the bride outfits and developments for 2022.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-5/research/je-marketing-(256).html
Tadashi Shoji is an effective name to look out for when you’re on the hunt for a designer dress.
https://digi610sa.z9.web.core.windows.net/research/digi610sa-(494).html
A stunning formal gown with cap sleeves and floral embroidery that trails from the excessive neckline to the floor-grazing hem.
https://je-tall-marketing-765.blr1.digitaloceanspaces.com/research/je-marketing-(328).html
Even as a guest to a wedding I even have made a few errors prior to now.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(322).html
You can present a little bit of cleavage, however too much can seem a bit inappropriate.
https://je-tall-marketing-794.fra1.digitaloceanspaces.com/research/je-marketing-(323).html
This mother’s knee-length patterned dress perfectly matched the mood of her kid’s outdoor wedding venue.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi496sa/o/research/digi496sa-(327).html
Try to find a long dress, and most significantly comfy.
https://storage.googleapis.com/digi470sa/research/digi470sa-(469).html
Plus, the silhouette of this gown will look that much more show-stopping because the cape wafts down the aisle to reveal her silhouette as she strikes.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-9/research/je-marketing-(444).html
Jovani Plus dimension mom of the bride dresses suits any physique sort.
https://je-tall-marketing-819.lon1.digitaloceanspaces.com/research/je-marketing-(252).html
Mother of the Bride and Groom dresses in the latest styles and colors.
https://digi661sa.netlify.app/research/digi661sa-(119)
In years gone by, being mother of the bride has meant frumpy frocks and ill-fitting dress suits, however no more!
https://storage.googleapis.com/digi459sa/research/digi459sa-(344).html
Another costume with ruching for you as I suppose ruched types are so flattering.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(90).html
I assume each of the above may work with winery weddings.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-6/research/je-marketing-(326).html
You can go for prints, and flowers should you like that type.
https://je-tall-marketing-787.lon1.digitaloceanspaces.com/research/je-marketing-(362).html
This brocade gown attracts the attention to all the proper places—from a hint of pores and skin on the shoulder to a ruched waist.
https://storage.googleapis.com/digi476sa/research/digi476sa-(318).html
This mixture is very great for summer weddings.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(140).html
This embellishment on this attractive dress provides a touch of magic excellent for any winter wedding.
https://digi599sa.z29.web.core.windows.net/research/digi599sa-(44).html
Your dress ought to complement or distinction the color scheme somewhat than match it.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(322).html
The delicate scoop neck and sheer lace sleeves are just some of the things we love about this A-line costume.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(348).html
For blogger Jenny Bernheim’s fancy rehearsal dinner, her mother wore a Carmen Marc Valvo dress, full with a beaded phantasm cut-out.
https://digi600sa.z45.web.core.windows.net/research/digi600sa-(452).html
So, go ahead, and let the pure shine of your dress communicate volume for you.
https://je-tall-marketing-820.lon1.digitaloceanspaces.com/research/je-marketing-(57).html
If you’ll find something with flowers even when it’s lace or embroidered.
https://je-tall-marketing-770.blr1.digitaloceanspaces.com/research/je-marketing-(20).html
Beach weddings tend to be barely more casual or bohemian in style than traditional weddings.
https://storage.googleapis.com/digi462sa/research/digi462sa-(195).html
Choose a robe with construction that holds its form all by itself.
https://je-tall-marketing-788.lon1.digitaloceanspaces.com/research/je-marketing-(461).html
The bride’s mom clearly had the color palette in thoughts when she chose this jade lace costume.
https://storage.googleapis.com/digi469sa/research/digi469sa-(145).html
The factor about the gold hue is that it is naturally attractive!
https://digi599sa.z29.web.core.windows.net/research/digi599sa-(462).html
Keep issues basic or try variations of the shades, like a champagne, rose gold, or shimmery charcoal.
https://je-tall-marketing-798.blr1.digitaloceanspaces.com/research/je-marketing-(18).html
In general, you’ll do your best to keep away from matching with the bridesmaids or the moms of the couple getting married.
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(187).html
MOB etiquettes say if black flatters you, all–black can be your go-to mother of the bride or mother of the groom in search of the special occasion.
https://storage.googleapis.com/digi465sa/research/digi465sa-(113).html
I was very impressed to see that there are stylish and chic outfits for all plus dimension women.
https://digi55sa.nyc3.digitaloceanspaces.com/research/digi55sa-(149).html
If you need the whole outfit then positively check out Dillards.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(211).html
Whatever the scenario, when you are able to attend a marriage, you’ll want to look your best.
https://je-tall-marketing-776.blr1.digitaloceanspaces.com/research/je-marketing-(348).html
It could additionally be your beloved has to wait to get married, or the occasion will be smaller.
https://je-sf-tall-marketing-707.b-cdn.net/research/je-marketing-(423).html
This mother wore a conventional hanbokwith floral and geometric embroidery to her daughter’s California ranch wedding.
https://digi74sa.sfo3.digitaloceanspaces.com/research/digi74sa-(21).html
Not certain the place to start with your search for that picture-perfect mother-of-the-bride dress?
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(153).html
The bridesmaids at this at-home Kentucky wedding ceremony sparkled in gold-sequined mini dresses.
https://je-tall-marketing-784.lon1.digitaloceanspaces.com/research/je-marketing-(325).html
When doubtful, go for a little black dress—but make it super luxe.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(206).html
There are plenty of choices out there for plus measurement mother of the bride clothes.
https://je-tall-marketing-787.lon1.digitaloceanspaces.com/research/je-marketing-(397).html
This glamorous gown in heat and wealthy gold enhances all skin tones and pairs beautifully with gold and silver equipment.
https://digi67sa.sfo3.digitaloceanspaces.com/research/digi66sa-(77).html
For warm-weather weddings and intimate affairs outdoor, fashion your bridal party—and most significantly, your mother—to the theme.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(212).html
You can match elegant strapless robes with gadgets such as a jacket or scarf.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(139).html
Not sure which shade will work to best coordinate the moms of the bride and groom with the remainder of the bridal party?
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(41).html
They have been excited about it since childhood, planning each…
https://storage.googleapis.com/digi473sa/research/digi473sa-(106).html
When in doubt, go for a little black dress—but make it super luxe.
https://digi72sa.sfo3.digitaloceanspaces.com/research/digi71sa-(240).html
Here are 10 of the best mother of the bride attire for this yr.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(79).html
MISSMAY creates stunning classic type attire that might be worn over and over again in almost any setting.
https://storage.googleapis.com/digi466sa/research/digi466sa-(131).html
Try to discover a lengthy dress, and most significantly comfy.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(108).html
Experiment with strapless types, surprising lengths, or fashionable jumpsuits.
https://je-sf-tall-marketing-715.b-cdn.net/research/je-marketing-(112).html
Sometimes, essentially the most classic and chic mom of the bride outfits aren’t attire at all!
https://digi73-1sa.sfo3.digitaloceanspaces.com/research/digi73sa-(431).html
We carry brands that excel in mom of the bride jacket clothes, capes and pantsuits, like Alex Evenings, R&M Richards and Ignite.
https://storage.googleapis.com/digi468sa/research/digi468sa-(46).html
Gold, black or navy footwear and equipment would look stylish.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
https://storage.googleapis.com/digi466sa/research/digi466sa-(357).html
As versatile as is elegant, this icy blue frock is the right transition piece to take you from the ceremony to the reception.
https://storage.googleapis.com/digi458sa/research/digi458sa-(467).html
The dress is figure-hugging and presents a easy silhouette.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(307).html
This is more of a personal alternative that is determined between you and your daughter.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(458).html
From modest attire to one thing with a bit more aptitude The Dress Outlet prides itself on having an in depth gallery of Mother of the Bride Dresses.
https://je-sf-tall-marketing-708.b-cdn.net/research/je-marketing-(185).html
We love spring colours like blush, gold, pale green, and blue together with floral prints for mom of the bride dresses for spring weddings.
https://digi597sa.z1.web.core.windows.net/research/digi597sa-(189).html
You might imagine it’s customary for the mom of the bride to wear an over-sized hat, but that’s merely not the case for 2022.
https://storage.googleapis.com/digi459sa/research/digi459sa-(284).html
Shop now through numerous retailers, together with official on-line shops.
https://digi651sa.netlify.app/research/digi651sa-(345)
You need her to really feel comfortable on the large day—especially when it’s time for marriage ceremony photos.
https://storage.googleapis.com/digi466sa/research/digi466sa-(450).html
Whether you could have your coronary heart on embroidery, embellishment, sequin, or ruched silk smoothness, golden dresses look nice in all styles and designs.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(64).html
This mom of the bride escorted her daughter down the aisle in a lightweight blue gorgeous halter gown.
https://je-sf-tall-marketing-710.b-cdn.net/research/je-marketing-(490).html
This costume is on the market in sizes 2 – 22 to fit a wide range of physique styles.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(389).html
An different is to mix black with another colour, which may look very chic.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(440).html
But for others, it’s restrictive, it feels too formal, and often, it ends up being rather expensive too.
https://je-tall-marketing-802.fra1.digitaloceanspaces.com/research/je-marketing-(261).html
It’s normally frequent apply to avoid sporting white, ivory or cream.
https://je-tall-marketing-791.sgp1.digitaloceanspaces.com/research/je-marketing-(288).html
Her mother, who equally sparkled in a gold silk dupioni floor-length skirt go properly with.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi498sa/o/research/digi498sa-(337).html
Also, in relation to a wedding, you wish to ensure that you don’t steal the bride’s thunder.
https://storage.googleapis.com/digi474sa/research/digi474sa-(242).html
I even have 2 youngsters who’ve definitely the age of getting maried 30 and 34.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi500sa/o/research/digi500sa-(266).html
Keep the lines of communication open all through the marriage planning course of.
https://storage.googleapis.com/digi459sa/research/digi459sa-(142).html
Go for prints that talk to your wedding location, and most significantly, her personal type.
https://digi76sa.sfo3.digitaloceanspaces.com/research/digi76sa-(494).html
Adhere to the costume code, and look to bridesmaids or the wedding robe for guidance on daring patterns or embellishments.
https://storage.googleapis.com/digi461sa/research/digi461sa-(496).html
Looking at summer season mom of the bride dresses which are a step away from the norm?
https://storage.googleapis.com/digi473sa/research/digi473sa-(337).html
If you haven’t heard from her by about five months earlier than the marriage, don’t be afraid to succeed in out and ask for an update on the costume code.
https://storage.googleapis.com/digi472sa/research/digi472sa-(500).html
With that in mind, you are absolutely entitled to want an outfit that lives as a lot as the special occasion.
https://storage.googleapis.com/digi464sa/research/digi464sa-(50).html
Celebrate their huge day in fashion with our Mother of the Bride or Groom outfits.
https://digi606sa.z48.web.core.windows.net/research/digi606sa-(283).html
This mom’s knee-length patterned costume perfectly matched the mood of her child’s outside wedding venue.
https://je-tall-marketing-775.tor1.digitaloceanspaces.com/research/je-marketing-(7).html
Sheer stretch tulle and cap sleeves on the neckline add an eye-catching element, giving the illusion of a strapless look.
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(408).html
If you need the whole outfit then definitely check out Dillards.
https://je-tall-marketing-776.blr1.digitaloceanspaces.com/research/je-marketing-(41).html
Neither a daytime occasion nor a formal summer night soiree requires a full-length gown.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi509sa/o/research/digi509sa-(274).html
The website’s sophisticated robes make for glorious evening put on that’ll serve you lengthy after the wedding day.
https://storage.googleapis.com/digi471sa/research/digi471sa-(346).html
Read our evaluations of 9 tie styles and colours, perfect in your wedding ceremony.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi498sa/o/research/digi498sa-(282).html
This mixture is very nice for summer weddings.
https://digi658sa.netlify.app/research/digi658sa-(262)
Opt for something current but timeless with clear traces.
https://digi609sa.z23.web.core.windows.net/research/digi609sa-(339).html
Discover our hand-picked assortment of mother of the bride attire and you’re guaranteed to be best-dressed – apart from the bride, of course!
https://storage.googleapis.com/digi458sa/research/digi458sa-(56).html
Her strapless and blush pink gown, with textured floral details and an embellished belt, had this mom smiling from ear to ear.
https://storage.googleapis.com/digi470sa/research/digi470sa-(482).html
Wear yours with heels in a neutral tone and delicate shoulder-grazing earrings.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(201).html
This gown is available in sizes 2 – 22 to suit quite a lot of body types.
https://digi652sa.netlify.app/research/digi652sa-(239)
You can complement it in a variety of methods, from a simple no-makeup look to daring pink lipstick paired with smokey eyes and much more.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-5/research/je-marketing-(422).html
The bridesmaids collected the recipes and created them right into a newlyweds cookery book that they gave the couple up their day.
https://je-tall-marketing-791.sgp1.digitaloceanspaces.com/research/je-marketing-(364).html
Check out our options for petite mom of the bride dresses!
https://digi606sa.z48.web.core.windows.net/research/digi606sa-(146).html
The contrast between these two gowns is in how they are selected.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(34).html
This will allow you to narrow down choices, making the buying process simpler.
https://digi608sa.z44.web.core.windows.net/research/digi608sa-(261).html
You should go for some shiny colors, or in case your daughter has a shade picked out for you then go along with that.
https://storage.googleapis.com/digi472sa/research/digi472sa-(268).html
Mothers of Bride and Groom often have a kind of ‘uniform’.
https://digi658sa.netlify.app/research/digi658sa-(21)
Of course, there’s more to your mother’s dress than just the beautiful details.
https://digi48sa.sfo3.digitaloceanspaces.com/research/digi48sa-(296).html
The beaded metallic tassels on this glimmering robe really got here into play when this mother took the dance ground.
https://digi660sa.netlify.app/research/digi660sa-(79)
Jovani presents you the highest highest quality MOB gowns for a low value.
https://je-sf-tall-marketing-710.b-cdn.net/research/je-marketing-(369).html
You do not want to wait till final minute to get your costume for your kid’s marriage ceremony.
https://je-tall-marketing-817.ams3.digitaloceanspaces.com/research/je-marketing-(97).html
The form of your costume can disguise every little thing from a small bust to massive hips.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(426).html
Carrie Crowell had come throughout the silk costume that her mother, country singer Rosanne Cash, wore at her 1995 wedding to Carrie’s stepfather.
https://digi610sa.z9.web.core.windows.net/research/digi610sa-(164).html
If you normally like clean, plain clothes, don’t go over the top with sequins and diamonds.
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-2/research/je-marketing-(301).html
If you’ll find something with flowers even if it’s lace or embroidered.
https://je-sf-tall-marketing-707.b-cdn.net/research/je-marketing-(10).html
Karen Kane has beautiful options that look slightly more casual if you are not looking for a full gown.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi502sa/o/research/digi502sa-(250).html
Sheer stretch tulle and cap sleeves at the neckline add an eye-catching detail, giving the phantasm of a strapless look.
https://digi604sa.z31.web.core.windows.net/research/digi604sa-(266).html
The entire collection is crafted with high quality fabrics for weddings or some other special occasion!
https://storage.googleapis.com/digi461sa/research/digi461sa-(459).html
A general rule for a marriage is that something too long or too short is a no-go.
https://digi599sa.z29.web.core.windows.net/research/digi599sa-(309).html
Saks is well probably the greatest department stores for buying a mother-of-the-bride costume.
https://digi605sa.z12.web.core.windows.net/research/digi605sa-(464).html
We’ve got all the recommendation and inspiration you have to discover the perfect mom-of-the-bride outfit.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(130).html
A little sparkle is a should when celebrating such a joyous occasion.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(170).html
Florals set on black or dark backgrounds feel no less romantic but actually deliver the delightfully unexpected.
https://storage.googleapis.com/digi466sa/research/digi466sa-(495).html
Its expansive variety, changing into match and classy design deem Montage the leader in Mother of the Bride and Mother of the Groom gown collections.
https://digi660sa.netlify.app/research/digi660sa-(30)
Purchases made through hyperlinks on this page could earn us a commission.
https://storage.googleapis.com/digi461sa/research/digi461sa-(71).html
The mother of the bride’s Oscar de la Renta robe was such a hit, it actually impressed the bridesmaids’ bouquets.
https://storage.googleapis.com/digi469sa/research/digi469sa-(216).html
This bride’s mom donned a stunning sari for her daughter’s wedding ceremony.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-8/research/je-marketing-(331).html
Beach weddings are extra laid-back and informal than different types of nuptials—and a proper costume would really feel out of place.
https://je-sf-tall-marketing-720.b-cdn.net/research/je-marketing-(44).html
One of the proudest and most anticipated days in a mother’s life is the day that her daughter or son will get married.
https://je-tall-marketing-814.sgp1.digitaloceanspaces.com/research/je-marketing-(139).html
Inspired by Old Hollywood glamour, it’s going to match proper in at a black tie wedding ceremony.
https://digi48sa.sfo3.digitaloceanspaces.com/research/digi48sa-(385).html
It’s usually widespread apply to avoid wearing white, ivory or cream.
https://storage.googleapis.com/digi458sa/research/digi458sa-(109).html
Both the mother of the bride and the mom of the groom selected putting gowns with embellishment and illusion necklines for this outside celebration.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(387).html
With palm leaf décor and plenty of vines, green was a primary theme throughout this charming and colorful South Carolina celebration.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(299).html
One of our favourite issues about Karen Kane is that they are dimension inclusive and have choices for all sizes.
https://digi55sa.nyc3.digitaloceanspaces.com/research/digi55sa-(90).html
Her strapless and blush pink gown, with textured floral details and an embellished belt, had this mother smiling from ear to ear.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(236).html
With over 3000 shops in the us and worldwide, buying has turn into really easy.
https://digi49sa.tor1.digitaloceanspaces.com/research/digi49sa-(215).html
Matching your MOB dress is a fun way to present you attention to element.
https://storage.googleapis.com/digi477sa/research/digi477sa-(435).html
For the mother whose type is glossy and minimal, go for a gown with an architectural silhouette in her favourite shade.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(361).html
This MOB gown falls just below the knee, so take the chance to show off a killer pair of heels.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(253).html
Looking at summer season mom of the bride clothes which are a step away from the norm?
https://storage.googleapis.com/digi474sa/research/digi474sa-(230).html
This black dress is perfect in case you are on the lookout for something more basic.
https://digi63sa.sfo3.digitaloceanspaces.com/research/digi63sa-(106).html
Regardless of her desire, likelihood is she has one, so ensure you know what it’s.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(494).html
From neutral off-white numbers to bold, punchy, and fashion-forward designs, there’s one thing right here that can go nicely with her fancy.
https://je-tall-marketing-793.tor1.digitaloceanspaces.com/research/je-marketing-(26).html
Karen Kane has stunning choices that look somewhat extra informal if you are not on the lookout for a full robe.
https://digi649sa.netlify.app/research/digi649sa-(166)
Look and feel truly elegant on this lengthy gown with out stealing all the eye from the bride.
https://storage.googleapis.com/digi470sa/research/digi470sa-(497).html
Saks is easily top-of-the-line department shops for purchasing a mother-of-the-bride dress.
https://storage.googleapis.com/digi477sa/research/digi477sa-(190).html
I would possibly play a job in my stepdaughter’s wedding or I might not.
https://je-tall-marketing-803.lon1.digitaloceanspaces.com/research/je-marketing-(271).html
Browse our high alternatives and buy your favorite proper on the spot.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(194).html
You’ve doubtless been by the bride’s aspect helping, planning, and lending invaluable advice alongside the way.
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(121).html
We love spring colours like blush, gold, pale green, and blue along with floral prints for mother of the bride clothes for spring weddings.
https://digi655sa.netlify.app/research/digi655sa-(86)
Read our evaluations of 9 tie styles and colors, excellent in your marriage ceremony.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(269).html
Straight-leg pants create a streamlined silhouette that subtly complements the velvet burnout-print top and jacket.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(478).html
If you prefer neutral tones, gold and silver clothes are promising selections for an MOB!
https://jekyll.s3.us-east-005.backblazeb2.com/20250729-4/research/je-marketing-(96).html
Discover the most effective marriage ceremony guest outfits for men and women for all seasons.
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(66).html
We even have tea-length clothes and long dresses to suit any season, venue or preference.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi506sa/o/research/digi506sa-(418).html
Keep in mind that many web sites permit you to filter attire by shade, silhouette, length, and neckline.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi503sa/o/research/digi503sa-(334).html
Try to discover a long costume, and most importantly comfy.
https://je-tall-marketing-783.blr1.digitaloceanspaces.com/research/je-marketing-(438).html
Speak with the bride to get her ideas on this and see what’s obtainable in shops and on-line.
https://digi611sa.z28.web.core.windows.net/research/digi611sa-(27).html
Her strapless and blush pink gown, with textured floral details and an embellished belt, had this mom smiling from ear to ear.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi496sa/o/research/digi496sa-(142).html
Not certain which shade will work to best coordinate the moms of the bride and groom with the remainder of the bridal party?
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(258).html
Express your love with handmade Valentine’s crafts like paper playing cards, gift concepts, and decorations.
https://digi59sa.ams3.digitaloceanspaces.com/research/digi59sa-(388).html
If you’ll find one thing with flowers even when it’s lace or embroidered.
https://storage.googleapis.com/digi464sa/research/digi464sa-(295).html
There usually aren’t any set guidelines when it comes to MOB outfits for the marriage.
https://digi59sa.ams3.digitaloceanspaces.com/research/digi59sa-(232).html
This retro and elegant cocktail costume includes a full-lace overlay excellent for an evening wedding ceremony.
https://je-tall-marketing-820.lon1.digitaloceanspaces.com/research/je-marketing-(295).html
This bride’s mother donned a beautiful sari for her daughter’s wedding.
https://digi655sa.netlify.app/research/digi655sa-(147)
It has over one hundred forty constructive critiques, many from women who wore this to a marriage and beloved it!
https://digi72sa.sfo3.digitaloceanspaces.com/research/digi71sa-(183).html
You do not need to wait until final minute to get your gown on your child’s wedding ceremony.
https://je-sf-tall-marketing-718.b-cdn.net/research/je-marketing-(176).html
—are any indication, that adage rings true, especially in relation to their very own wedding fashion.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(28).html
Embellished with stunning ornate beading, this robe will catch the sunshine from each angle.
https://digi602sa.z45.web.core.windows.net/research/digi602sa-(102).html
A stylishly simple occasion costume printed with romantic florals, perfect for the mother of the bride.
https://digi647sa.netlify.app/research/digi647sa-(71)
You should go for some shiny colors, or in case your daughter has a colour picked out for you then go along with that.
https://digi607sa.z44.web.core.windows.net/research/digi607sa-(481).html
Its bateau neckline, three-quarter size sleeves, and full A-line skirt make it flattering, as well.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi510sa/o/research/digi510sa-(365).html
Let the answers to a few of our most regularly asked questions information you in the proper direction.
https://digi647sa.netlify.app/research/digi647sa-(453)
Find the best tie styles for 2021 and past on your wedding.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(244).html
This gown comes with a sweater over that may be taken off if it gets too sizzling.
https://storage.googleapis.com/digi475sa/research/digi475sa-(184).html
Keep issues basic or strive variations of the shades, like a champagne, rose gold, or shimmery charcoal.
https://je-tall-marketing-809.lon1.digitaloceanspaces.com/research/je-marketing-(288).html
Its expansive selection, turning into fit and classy design deem Montage the leader in Mother of the Bride and Mother of the Groom costume collections.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi497sa/o/research/digi497sa-(358).html
We asked some wedding ceremony trend experts to determine what a MOB should put on on the large day.
https://je-tall-marketing-799.lon1.digitaloceanspaces.com/research/je-marketing-(456).html
Of course, you can play with colours of sequin outfits to kick off the look of your goals.
https://storage.googleapis.com/digi466sa/research/digi466sa-(451).html
You can nonetheless embrace these celebratory metallic shades with out overlaying yourself head to toe in sequins.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(77).html
For a beautiful look, select a celebratory design that includes lace and lengthy sleeves.
https://storage.googleapis.com/digi467sa/research/digi467sa-(442).html
Dillards is a great place to examine out if you’re in search of one thing greater end.
https://storage.googleapis.com/digi474sa/research/digi474sa-(134).html
Mothers of Bride and Groom usually have a type of ‘uniform’.
https://digi656sa.netlify.app/research/digi656sa-(338)
As the groom’s mom, you’ll want to let the mom of the bride take the lead during the gown shopping process.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(14).html
Opt for a well-cut, flowing sundress in a breathable fabric—and pair with dressy sandals to drag the look collectively (while still feeling snug on the sand!).
https://je-tall-marketing-822.sgp1.digitaloceanspaces.com/research/je-marketing-(260).html
Your gown should complement or distinction the colour scheme quite than match it.
https://je-tall-marketing-814.sgp1.digitaloceanspaces.com/research/je-marketing-(371).html
This glamorous gown in warm and rich gold enhances all pores and skin tones and pairs superbly with gold and silver equipment.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(256).html
So, in case your youngsters are hosting a black tie affair, make certain to wear a floor-length gown—preferably in a neutral tone .
https://digi62sa.sfo3.digitaloceanspaces.com/research/digi62sa-(266).html
Keep in mind that many web sites allow you to filter clothes by colour, silhouette, size, and neckline.
https://storage.googleapis.com/digi460sa/research/digi460sa-(437).html
This beautiful floral frock would make the right complement to any nature-inspired wedding ceremony.
https://je-tall-marketing-800.syd1.digitaloceanspaces.com/research/je-marketing-(468).html
You’ll merely glow in this shimmering gold gown by Aidan Mattox.
https://storage.googleapis.com/digi467sa/research/digi467sa-(410).html
Saks is easily top-of-the-line department shops for getting a mother-of-the-bride dress.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(453).html
To achieve the right balance of consolation and ritual, we’ve included tea length mother of the bride clothes, too.
https://je-tall-marketing-780.blr1.digitaloceanspaces.com/research/je-marketing-(109).html
This retro and stylish cocktail gown contains a full-lace overlay excellent for a night wedding ceremony.
https://digi657sa.netlify.app/research/digi657sa-(42)
Many of the choices above would allow you to to cover slightly bit of a tummy.
https://je-tall-marketing-776.blr1.digitaloceanspaces.com/research/je-marketing-(332).html
The capelet dress is good if you wish to cowl up your upper arms.
https://storage.googleapis.com/digi458sa/research/digi458sa-(189).html
One of our favorite issues about Karen Kane is that they are dimension inclusive and have choices for all sizes.
https://digi78sa.sfo3.digitaloceanspaces.com/research/digi78sa-(63).html
This desert coloured gown is ideal if what the bride wants is for you to wear a colour nearer to white.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(87).html
So, at the very least, both mothers will want to put on colors that complement the opposite.
https://digi598sa.z8.web.core.windows.net/research/digi598sa-(396).html
Dresses are made in stunning colors similar to gold, pink, and blue and mom of the bride dresses.
https://je-tall-marketing-801.sgp1.digitaloceanspaces.com/research/je-marketing-(243).html
We’ve rounded up a few of the fairly Mother-of-the-Bride clothes to put on for spring weddings.
https://je-tall-marketing-778.fra1.digitaloceanspaces.com/research/je-marketing-(226).html
Go for prints that speak to your marriage ceremony location, and most significantly, her private fashion.
https://storage.googleapis.com/digi468sa/research/digi468sa-(395).html
Fall and winter weddings name for stylish muted tones like silvery grey.
https://je-tall-marketing-812.fra1.digitaloceanspaces.com/research/je-marketing-(426).html
We’re in love with the muted florals on this romantic mother-of-the-bride gown.
https://je-tall-marketing-813.syd1.digitaloceanspaces.com/research/je-marketing-(244).html
The bridesmaids at this at-home Kentucky wedding ceremony sparkled in gold-sequined mini dresses.
https://je-tall-marketing-816.blr1.digitaloceanspaces.com/research/je-marketing-(283).html
Discover one of the best marriage ceremony guest outfits for men and women for all seasons.
https://je-tall-marketing-814.sgp1.digitaloceanspaces.com/research/je-marketing-(257).html
Inspired by bold flowers, a blooming print pops off each inch of this strapless ball robe, from the illusion plunge corset bodice to the total, sweeping skirt.
https://digi601sa.z45.web.core.windows.net/research/digi601sa-(432).html
It’s your duty to grasp what she wants from both you and the groom’s mom in phrases of your apparel.
https://digi61sa.nyc3.digitaloceanspaces.com/research/digi61sa-(56).html
This funky floral print mother-of-the-bride gown provides us all the ’70s vibes .
https://digi60sa.fra1.digitaloceanspaces.com/research/digi60sa-(483).html
Purchases made via hyperlinks on this page might earn us a fee.
https://storage.googleapis.com/digi461sa/research/digi461sa-(269).html
Find the proper tie types for 2021 and past on your wedding ceremony.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(280).html
Pink anemones and blue and yellow wildflower buds accented this beautiful black dress worn by the mom of the bride.
https://je-tall-marketing-787.lon1.digitaloceanspaces.com/research/je-marketing-(311).html
One of our favourite issues about Karen Kane is that they are measurement inclusive and have choices for all sizes.
https://digi656sa.netlify.app/research/digi656sa-(388)
Spring and summer weddings name for soft tones, floral motifs, and a romantic aptitude.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi504sa/o/research/digi504sa-(118).html
Of course, there’s more to your mother’s costume than just the pretty details.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(38).html
Colors such as fuchsia, green and silver are just a few ideas!
https://digi75sa.sfo3.digitaloceanspaces.com/research/digi75sa-(39).html
With a mild match at the hips, this costume is designed to flatter you in all the best places.
https://digi64sa.sfo3.digitaloceanspaces.com/research/digi64sa-(145).html
In short, yes, but only if it goes with the texture of the day.
https://digi658sa.netlify.app/research/digi658sa-(216)
After all, you don’t wish to mix in with the bridesmaids and event decor.
https://digi57sa.sfo3.digitaloceanspaces.com/research/digi57sa-(209).html
Our moms are attractive and amazing and they want to rock what they’ve.
https://je-tall-marketing-811.fra1.digitaloceanspaces.com/research/je-marketing-(482).html
It is also really helpful to keep away from black clothes as those usually symbolize instances of mourning.
https://storage.googleapis.com/digi474sa/research/digi474sa-(430).html
You can complement it in a number of ways, from a easy no-makeup look to daring purple lipstick paired with smokey eyes and a lot more.
https://storage.googleapis.com/digi469sa/research/digi469sa-(322).html
The champagne coloured ankle-length wrap costume looks stunning on this mother of the bride.
https://digi56sa.sfo3.digitaloceanspaces.com/research/digi56sa-(174).html
Weddings are very particular days not just for brides and grooms, however for his or her mothers and grandmothers, too.
https://digi58sa.ams3.digitaloceanspaces.com/research/digi58sa-(304).html
We’ve at all times heard that mother is aware of greatest, and if these moms of the bride—and mothers of the groom!
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi505sa/o/research/digi505sa-(46).html
Weddings could also be very totally different proper now, relying on the place you reside.
https://digi600sa.z45.web.core.windows.net/research/digi600sa-(446).html
You can still embrace those celebratory metallic shades with out covering yourself head to toe in sequins.
https://digi63sa.sfo3.digitaloceanspaces.com/research/digi63sa-(199).html
The capelet costume is good if you like to cowl up your higher arms.
https://storage.googleapis.com/digi467sa/research/digi467sa-(211).html
As the mom of the bride, eyes will be on you almost as a lot as they are going to be on the pleased couple.
https://digi659sa.netlify.app/research/digi659sa-(217)
With palm leaf décor and a lot of vines, green was a major theme all through this charming and colorful South Carolina celebration.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi508sa/o/research/digi508sa-(198).html
This will complete your outfit and produce it collectively as a whole.
https://digi654sa.netlify.app/research/digi654sa-(286)
Stylish blue navy dress with floral sample lace and fantastic silk lining, three-quarter sleeve.
https://digi650sa.netlify.app/research/digi650sa-(112)
The mother of the bride gown gallery has a costume for each budget and each body sort together with plus sizes.
https://storage.googleapis.com/digi476sa/research/digi476sa-(84).html
This two-piece silhouette style flows fantastically over the body and has a v-shaped again opening that closes with a concealed zipper.
https://digi51sa.ams3.digitaloceanspaces.com/research/digi51sa-(132).html
This materials is nice as a end result of it lays flattering and looks great in photos.
https://digi72sa.sfo3.digitaloceanspaces.com/research/digi71sa-(386).html
The glossy silk material glides seamlessly over your figure, however an ankle-length skirt, high neckline and draped sleeves maintain issues modest.
https://digi650sa.netlify.app/research/digi650sa-(467)
David’s Bridal provides handy online and in-person buying experiences.
https://digi608sa.z44.web.core.windows.net/research/digi608sa-(118).html
This outfit’s intricate corded embroidery and understated black skirt are a match made in heaven—just like your daughter and their soon-to-be spouse.
https://storage.googleapis.com/digi469sa/research/digi469sa-(166).html
Your costume should complement or distinction the colour scheme rather than match it.
https://digi70sa.sfo3.digitaloceanspaces.com/research/digi30sa-(205).html
Find jacket dresses in champagne, orchid, pink, lavender, or navy for girls of all ages.
https://digi603sa.z11.web.core.windows.net/research/digi603sa-(153).html
Her strapless and blush pink gown, with textured floral details and an embellished belt, had this mom smiling from ear to ear.
https://digi77sa.sfo3.digitaloceanspaces.com/research/digi77sa-(391).html
This deco-inspired gown will shimmer in photographs and stun on the dance flooring.
https://digi604sa.z31.web.core.windows.net/research/digi604sa-(425).html
Dresses are made in beautiful colours corresponding to gold, purple, and blue and mother of the bride dresses.
https://storage.googleapis.com/digi474sa/research/digi474sa-(381).html
Beading in tones of blue, grey, and silver add dimension and complicated sparkle to this flattering mesh column robe.
https://je-tall-marketing-822.sgp1.digitaloceanspaces.com/research/je-marketing-(261).html
Mother of the Bride and Groom dresses within the latest types and colors.
https://digi57sa.sfo3.digitaloceanspaces.com/research/digi57sa-(365).html
This additionally helps depart time for delivery in case the dress takes longer than anticipated to arrive.
https://digi68sa.sfo3.digitaloceanspaces.com/research/digi68sa-(395).html
It’s important to ensure that any head items don’t swamp your frame, and doesn’t hide your face.
https://je-sf-tall-marketing-733.b-cdn.net/research/je-marketing-(357).html
As mom of the bride, you may want to discover a look which enhances these components, without being matchy-matchy.
https://digi661sa.netlify.app/research/digi661sa-(166)
You’ll find understated A-line dresses and fabulous sheath numbers.
https://je-tall-marketing-772.sgp1.digitaloceanspaces.com/research/je-marketing-(116).html
Of course, there’s more to your mom’s costume than simply the gorgeous details.
https://digi69sa.sfo3.digitaloceanspaces.com/research/digi69sa-(146).html
A general rule for a wedding is that something too long or too short is a no-go.
https://storage.googleapis.com/digi463sa/research/digi463sa-(135).html
In addition, many kinds are available with matching jackets or shawls for final versatility.
https://je-tall-marketing-765.blr1.digitaloceanspaces.com/research/je-marketing-(86).html
It has a beautiful reduce that enhances all the right places.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi502sa/o/research/digi502sa-(190).html
With a gentle fit at the hips, this dress is designed to flatter you in all the right places.
https://digi53sa.sgp1.digitaloceanspaces.com/research/digi53sa-(4).html
Mother of the groom clothes are down to private alternative on the day.
https://digi52sa.fra1.digitaloceanspaces.com/research/digi52sa-(291).html
They are a fantastic place to take a look at if you’re in search of good high quality clothes.
https://digi65sa.sfo3.digitaloceanspaces.com/research/digi65sa-(14).html
The beaded flowers down one aspect add a tactile touch of luxurious to the column gown .
https://digi611sa.z28.web.core.windows.net/research/digi611sa-(387).html
This mixture is particularly great for summer season weddings.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi505sa/o/research/digi505sa-(117).html
This mixture is very great for summer weddings.
https://jekyll.s3.us-east-005.backblazeb2.com/20250730-7/research/je-marketing-(397).html
Then you’ll view your saved listings every time you login.
https://digi600sa.z45.web.core.windows.net/research/digi600sa-(243).html
The capelet costume is right should you prefer to cover up your upper arms.
https://storage.googleapis.com/digi470sa/research/digi470sa-(46).html
Otherwise, photos will appear off-balanced, and it might be misconstrued that one mother is making an attempt to outshine or outdo the opposite.
https://digi649sa.netlify.app/research/digi649sa-(219)
One reviewer mentioned they wore a white jacket excessive but you would also select a wrap or bolero.
https://objectstorage.ap-tokyo-1.oraclecloud.com/n/nrswdvazxa8j/b/digi499sa/o/research/digi499sa-(346).html
As a mother, watching your son or daughter get married will be one of the joyful experiences in your life.
https://storage.googleapis.com/digi462sa/research/digi462sa-(213).html
But an important piece of apparel you will select main up to your child’s wedding?
https://digi74sa.sfo3.digitaloceanspaces.com/research/digi74sa-(19).html
This mother of the bride donned an attractive light grey robe with an illusion neckline brimming with stunning beaded detailing.
https://je-tall-marketing-784.lon1.digitaloceanspaces.com/research/je-marketing-(199).html
They have been excited about it since childhood, planning every…
https://je-tall-marketing-810.fra1.digitaloceanspaces.com/research/je-marketing-(126).html
As the groom’s mother, you’ll need to let the mom of the bride take the lead through the dress buying process.
พีจีสล็อต สล็อตแตกยับ!
รวยได้ทุกวัน แค่ปลายนิ้วก็รวยได้!,หมดปัญหาเกมสล็อตทำเงินยาก!
ลอง PGSLOT สิ! ทำเงินได้ไว รับทรัพย์เต็มๆ,
รีบเลย! ค่าย PG แจกหนัก ทุกคนที่สมัคร,ทุนน้อยก็รวยได้!
พีจีสล็อต เกมสล็อตยอดนิยม กำไรงาม จ่ายเต็ม,สมัคร PGSLOT
เลย! โกยกำไรมหาศาล ไม่ต้องรอ,
สุดยอดเกมสล็อตและโบนัสจัดเต็ม มีแค่ PGSLOT ที่เดียว!,
พีจีสล็อต: คืนยอดเสียสูงสุด!
คุ้มกว่านี้ไม่มีอีกแล้ว ไม่มีอะไรจะคุ้มไปกว่านี้แล้ว,สมัครวันนี้ รับเลย!
พีจีสล็อต จัดเต็มโบนัสต้อนรับสมาชิกใหม่ รับเองง่ายๆ,พลาดไม่ได้!
PGSLOT โปรโมชั่นเด็ดประจำสัปดาห์ แจกเครดิตฟรีไม่อั้น,ลงทุนน้อยได้มากกับ PGSLOT!
โบนัสสุดคุ้ม ไม่อั้น!,PGSLOT ชวนเพื่อนมาเล่น ได้เงินง่ายๆ แค่ชวนเพื่อน!,คุ้มยิ่งกว่าคุ้ม!
เล่น PGSLOT ได้กำไรแน่นอน โปรโมชั่นเยอะ โบนัสแยะ,
สนุกกับ PGSLOT ได้ทุกที่!
เล่นได้บนมือถือและคอมพิวเตอร์
รองรับทุกระบบ!,มั่นใจ 100%!
พีจีสล็อต เว็บตรง ไม่ผ่านเอเย่นต์ ฝาก-ถอนออโต้ ฉับไว!,บริการประทับใจ 24 ชม.!
แอดมินใจดี ใส่ใจทุกปัญหา,พีจีสล็อต
เว็บสล็อตยอดนิยม มั่นคงและเชื่อถือได้,เริ่มเล่น PGSLOT ได้เลย ไม่ต้องโหลดแอพให้ยุ่งยาก สะดวกสบายสุดๆ,เล่นเกมไม่มีกระตุก!
พีจีสล็อต เล่นมันส์ไม่มีเบื่อ,
ลองมาแล้ว PGSLOT โบนัสเข้าตลอด เล่นแล้วรวย!,บริการ PGSLOT ดีเยี่ยม!
ไม่ต้องรอนานเลย ไม่ต้องรอนานเลย,เจอแล้วเกมสล็อตที่ใช่!
PGSLOT ภาพสวย เสียงคมชัด ทำกำไรได้เยอะ!,รีวิวจากผู้เล่นจริง!
PGSLOT ไม่ทำให้ผิดหวัง สุดยอดจริงๆ!,
ใครยังไม่ลอง PGSLOT ถือว่าพลาดมาก!
โอกาสทำเงินดีๆ รอคุณอยู่,เว็บสล็อต pg เว็บตรงที่ดีที่สุดในตอนนี้!
PGSLOT มีแต่เกมมันส์ๆ
เพลินตลอด!
https://storage.googleapis.com/digi467sa/research/digi467sa-(96).html
It is customary to keep away from carrying white in your children’s wedding day.
Immerse into the stunning universe of EVE Online. Find your fleet today. Create alongside millions of pilots worldwide. Join now
cash frenzy free slots, united statesn casino minimum deposit dollar 10 and
uk best online slots, or live online roulette united states
Also visit my web blog; Goplayslots.net
Большое спасибо! Ценно материал.
My web blog https://www.hotel-in-freudenberg.de/
united statesn online pokies review, spin usa Distance To Coushatta Casino (https://Estudiantevirtual.Pucv.Cl) and online
poker canada two plus two, or free casino chips usa
free bingo no deposit win real money united states, personal gambling licence usa and
australian online no deposit casino, or bet365 play united statesn roulette dollar blackjack online uk
best usa online turtle creek casino military discount, Roxie, real money, online
casino united states 1 dollar deposit and lucky lusae slot machine,
or usa super casino
is ipamorelin better than sermorelin
References:
http://stroyrem-master.ru/user/planetping67/
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
sms casino deposit australia, united states roulette rules How to Play Blackjack and win money usa casino fast withdrawal,
or deposit 10 get usa
paying tax on gambling winnings canada, united kingdom poker league ceo and best online the crown casino accommodation (Hildred) united kingdom real money,
or united statesn online no deposit pokies
australian online play Casino online in japan min deposit $10, sweet bonausaa online slot and online casinos that accept apple pay usa, or nz online casinos that accept paypal
I’ll definitely be coming back for more. Watch wontumi tv sports time today — Ghanaian TV with sports and news. HD streaming with low latency. replays, program schedule, studio discussions. Including today’s schedule. simple interface and quick start.
to buy united statesn casino guide, usa will
a casino cash a stimulus check (Kurt) sign up bonus and real money online casino canada app, or bet365 new zealandn roulette tips
wettstrategie beste sportwetten vorhersagen (testwp.helium.sh)
online sportwetten tipps
My webpage … basketball wetten quoten
wettbüro bielefeld
My blog – Sportwetten öSterreich Anbieter
esport Wetten strategie – credencerealtorsltd.com
– asiatisch tore
ecken App Wetten Mit Freunden anbieter
wetten doppelte chance
Here is my blog :: sportwetten Kombiwetten tipps
sportwetten prognosen heute
My web site – Wette Spiel
spiel wetten
Also visit my web blog :: sportwetten Tippen
sportwetten anbieter paysafecard
Here is my site wettanbieter bonus
sportwette ohne oasis
Feel free to surf to my blog: us wahl wetten quote – Aline –
buchmacher app
My website … neuer Wettanbieter
online sportwetten bonus wettanbieter ohne lugas mit paysafecard, https://letsbdgo.Xyz/2025/10/usa-football-bet,
einzahlung
wettquoten biathlon
Look into my web blog sportwetten Online österreich
live Online Wetten Ohne Einzahlung quoten
online sportwetten schleswig holstein
Feel free to surf to my website; halbzeit endstand wetten strategie
(nexacreative.lk)
Sportwetten seite lizenz kaufen
sportwetten schweiz kiosk
Check out my web site – Wett Tipps üBer Unter Tore
wetten österreich
Here is my webpage wettstrategien sportwetten – Kerri –
buchmacher quotenvergleich
Here is my homepage; sportwetten mit startguthaben Ohne einzahlung
sportwetten beste anbieter
Feel free to surf to my site – wett online; Aileen,
wettbüro
Visit my website: Sportwetten Interwetten
Sportwetten Neukundenbonus Vergleich tipps von profis
krypto wettanbieter
Feel free to visit my homepage sportwetten Schweiz Online
live sport wetten
Also visit my homepage deutsche sportwetten lizenz
I read this piece of writing fully on the topic of
the difference of hottest and preceding technologies, it’s awesome
article.
Feel free to surf to my web blog; lottery game app win real money (Terese)
tipp Wetten mit bonus ohne Einzahlung (http://WWW.Farmaciaferonia.ro) vorhersage
dfb pokal quoten wetten
Here is my web-site – beste bonus wettanbieter
gute wettseiten
Also visit my web page; buchmacher england (https://lichenlekar.com)
what is a steroid cycle
References:
https://w2k.sh/guycardoza1184
wettanbieter gratiswette
my web site – kombiwetten heute (Tammi)
betibet sportwetten online deutschland
My page – gute wettseiten
sportwetten tipp (http://www.Yantraharvest.Com) tipps telegram
sichere sportwetten heute
my blog post; wetten dass quote
online wettanbieter österreich
my blog; buchmacher werden, http://www.Tristatenoahproject.org,
handicap bei wetten
my web page – sportwetten deutschland ohne oasis – https://inmetal.com.Br/eucasino-sportwetten-bonus-ohne-einzahlung/,
gute wett tipps
Review my web-site: größTe wettanbieter in deutschland
kombiwette
my homepage quoten beim wetten (Santos)
wettbüro maximale auszahlung
Here is my blog was ist Ein buchmacher
was heißT handicap beim wetten; https://www.op4ideas.it/deutschland-osterreich-eishockey-liveticker, anbieter
willkommensbonus ohne einzahlung wetten
My homepage beste wettanbieter test betrugstest (Stacey)
Смотрите порно безопасно, выбирая
проверенные веб-сайты для взрослых.
Используйте надежные порнохабы для конфиденциального развлечения.
my web blog BUY VALIUM ONLINE
Просматривайте откровенные материалы безопасно,
выбирая проверенные веб-сайты для взрослых.
Используйте безопасные платформы для конфиденциального развлечения.
Here is my blog … buy valium online
Контент для взрослых можно транслировать на
надежных платформах для обеспечения конфиденциальности.
Откройте для себя безопасные
веб-сайты для качественного просмотра.
Feel free to surf to my page … buy valium online
Сайт с контентом для взрослых предлагает широкий
выбор видео для взрослых развлечений.
Выбирайте безопасные сайты для взрослых
для конфиденциального опыта.
My web page :: BUY VIAGRA
Темы для взрослых широко доступен на специализированных платформах для зрелой
аудитории. Выбирайте гарантированные источники для
обеспечения безопасности.
My page – buy valium online